Guide to navigate administrative operations in RDA Fabric platform's UI Portal
1. RDA Fabric Platform's UI Portal Introduction
The RDAF platform's UI portal is the primary interface for performing various administration operations, including but not limited to.
- RDA Fabric Artifact Configuration & Management
- Pipelines
- Credentials
- Service Blueprints
- Formatting Templates
- Synthetics
- Bundles
- RDA Fabric Data Management
- Persistent Streams
- Datasets
- Log Archives
- Dependency Mappings
- Data Staging Area
- RDA Fabric Applications (OIA/AIA) on-boarding
- RDA Fabric Operational Dashboard
- RDA Fabric User Administration (RBAC)
- RDA Fabric User Dashboard Configuration & Management
2. RDA Fabric User Administration (RBAC)
As part of the installation of RDAF core platform services, it creates a default tenant admin user called admin@cfx.com
In order to access RDAF UI portal, open a web browser and type the RDAF HAProxy server's IP address or DNS Name if it is a non-HA deployment or RDAF HAProxy server's virtual IP address or DNS Name if it is an HA deployment as shown below.
The default password for admin@cfx.com is admin1234
Note
admin@cfx.com user is the super admin user for RDA Fabric platform. For production deployment, please make sure to provide strong password and limit the access only to designated administrative users.
On first login onto RDAF UI portal, it prompts for resetting the above default password to user's choice.
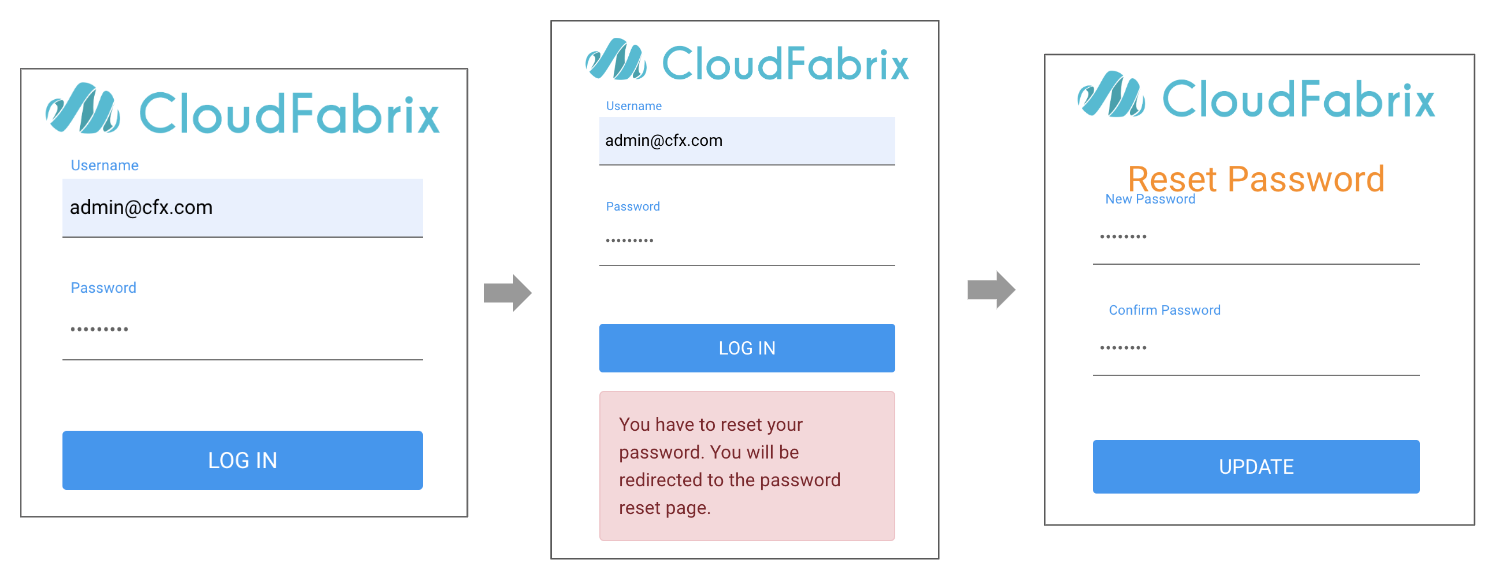
2.1 Local Users
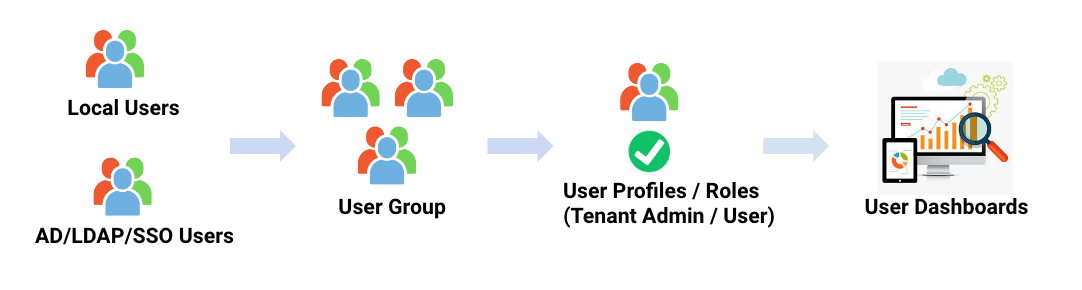
RDA Fabric platform support local users and remote users integrating with external identity and access management (IAM) tools. Below are supported for user access management.
- Local Users
- Active Directory Users
- SSO Users
Local Users are created and managed within the RDAF platform.
Note
Local Users should be used only for POC or Demo or Development environments. For Production deployments, it is recommended to integrate with external identity and access management tools such as Active Directory / LDAP or SSO
The below picture illustrates how the RDAF platform users (local/ or remote) are mapped and roles / permissions are assigned.
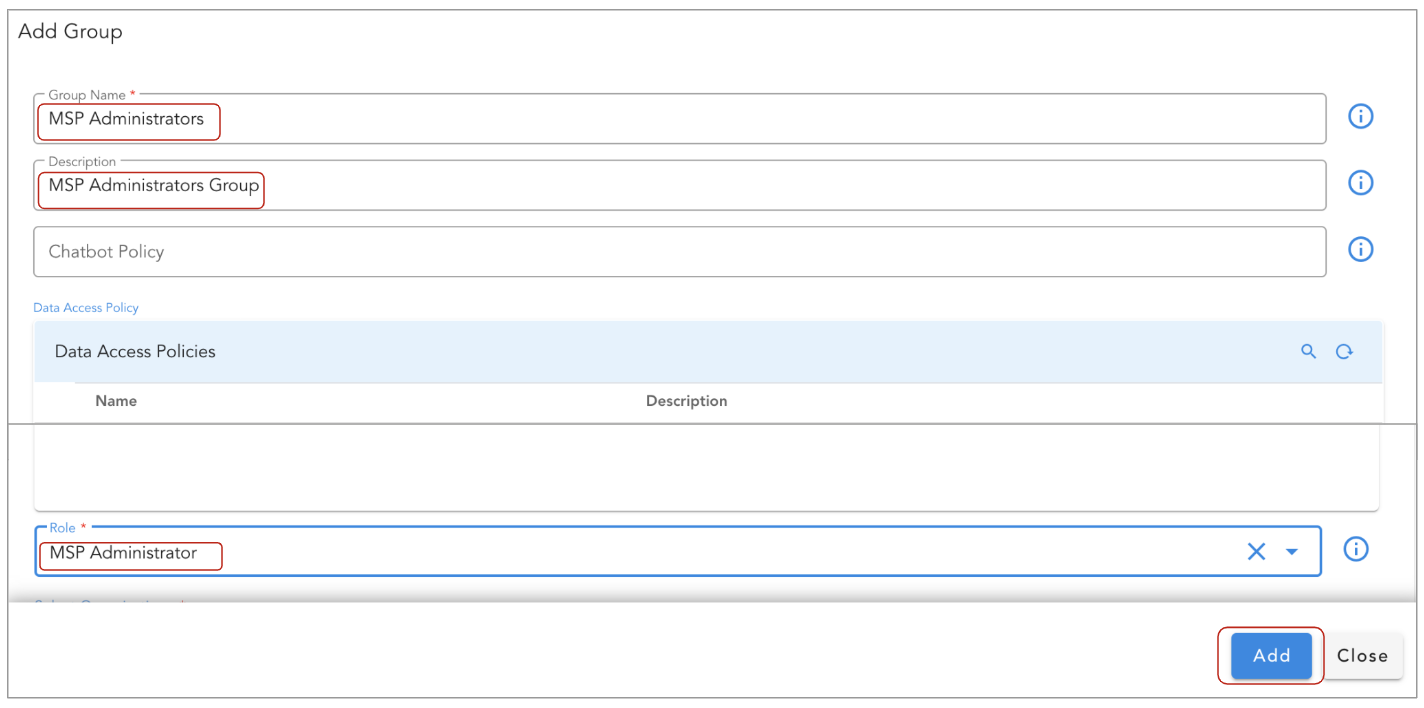
Adding MSP User Group:
After login into RDAF platform using admin@cfx.com user, go to Main Menu --> Administration --> Users
Under User Groups section, click on Add Group action button to create a new user group for MSP Administration
- Enter Group Name as MSP Administrators
- Enter Description as MSP Administration Group
- Select Role as MSP Administrator
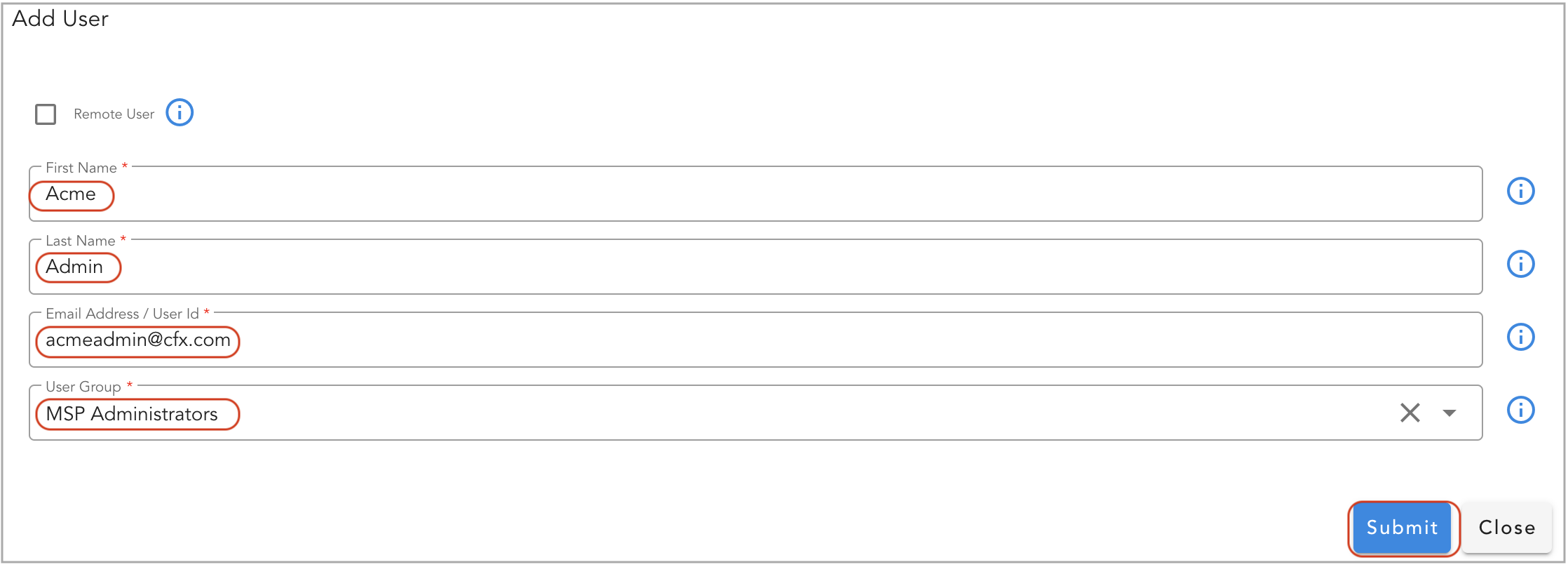
Adding MSP User:
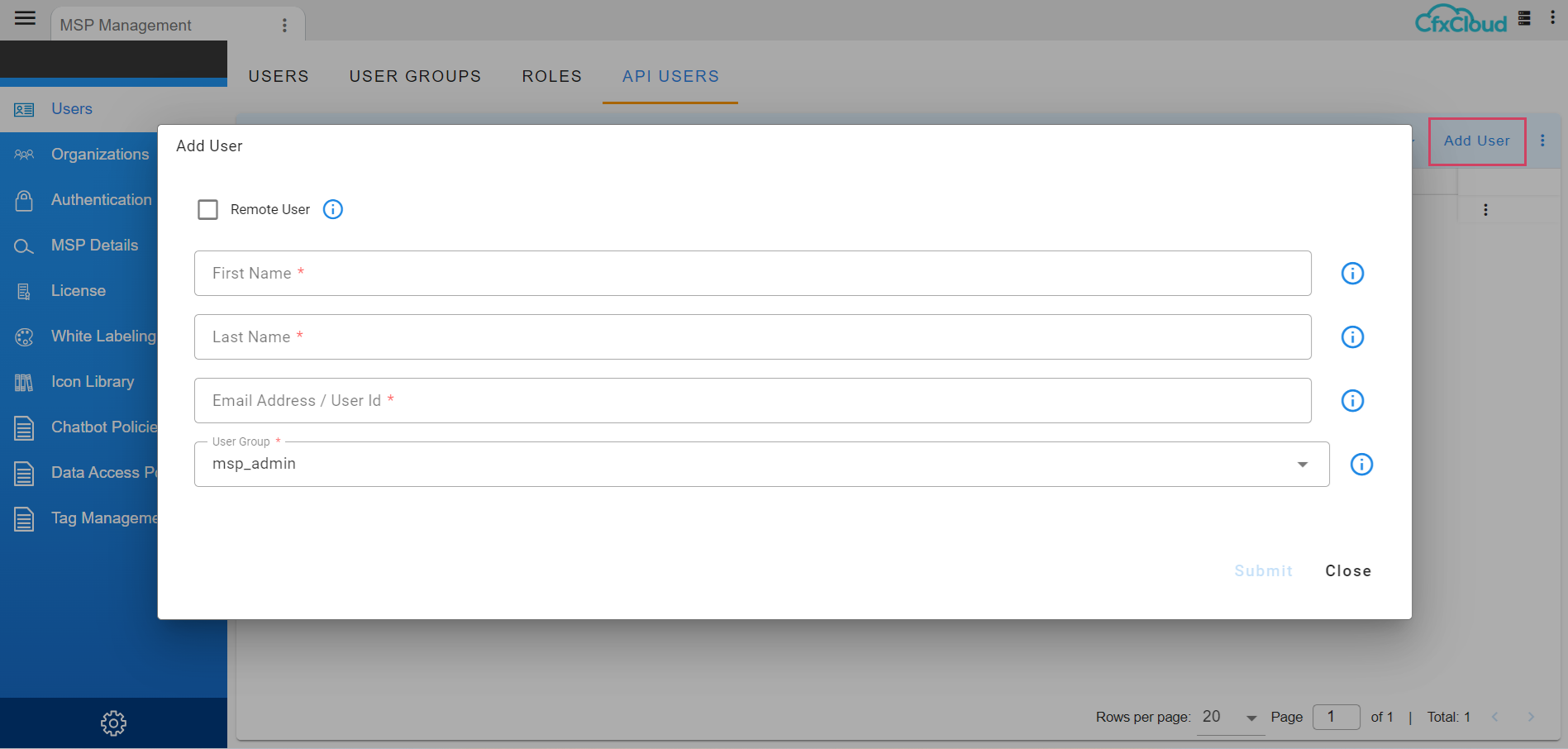
Under Users section, click on Add User action button to create a new MSP user.
- Enter User First and Last Name
- Enter User's email address (it is used as login if for the user)
- Select User Group as MSP Administrators (as created above)
RDAF platform by default comes with the below User Profiles / Roles which can be associated to an appropriate user groups as per the requirement.
- MSP Administrator: When MSP Administrator role is associated to an User Group, all the associated users to it will have full MSP Administration privileges and will have access to all of the RDAF platform's Menu items.
- MSP User: When MSP User role is associated to an User Group, all the associated users to it will have limited MSP privileges and will have access to all of the RDAF platform's Menu items.
- MSP Read Only User: When MSP Read Only User role is associated to an User Group, all the associated users to it will have read-only MSP privileges and will have access to all of the RDAF platform's Menu items.
- Organization Administrator: When Organization Administrator role is associated to an User Group, all the associated users to it will have Administrative privileges to the resources within the selected Organization.
- Organization User: When Organization User role is associated to an User Group, all the associated users to it will have limited privileges to the resources within the selected Organization.
- Organization Read Only User: When Organization Read Only User role is associated to an User Group, all the associated users to it will have read-only privileges to the resources within the selected Organization.
- L1 User: When L1 User role is associated to an User Group, all the associated users to it will have limited privileges and will have ONLY access to RDAF platform's Dashboards Menu.
- L3 User: When L3 User role is associated to an User Group, all the associated users to it will have limited privileges and will have ONLY access to RDAF platform's Dashboards Menu.
2.2 Active Directory Users
RDA Fabric platform supports integrating with Windows Active Directory IAM (Identity and Access Management) system.
For integrating with Windows Active Directory, go to Main Menu --> Administration --> Authentication Servers
Under Authentication Servers section, click on Add button to add Windows Active Directory server details.
Click on Test Connectivity button to validate the Active Directory integration before clicking on Add button to save the configuration.
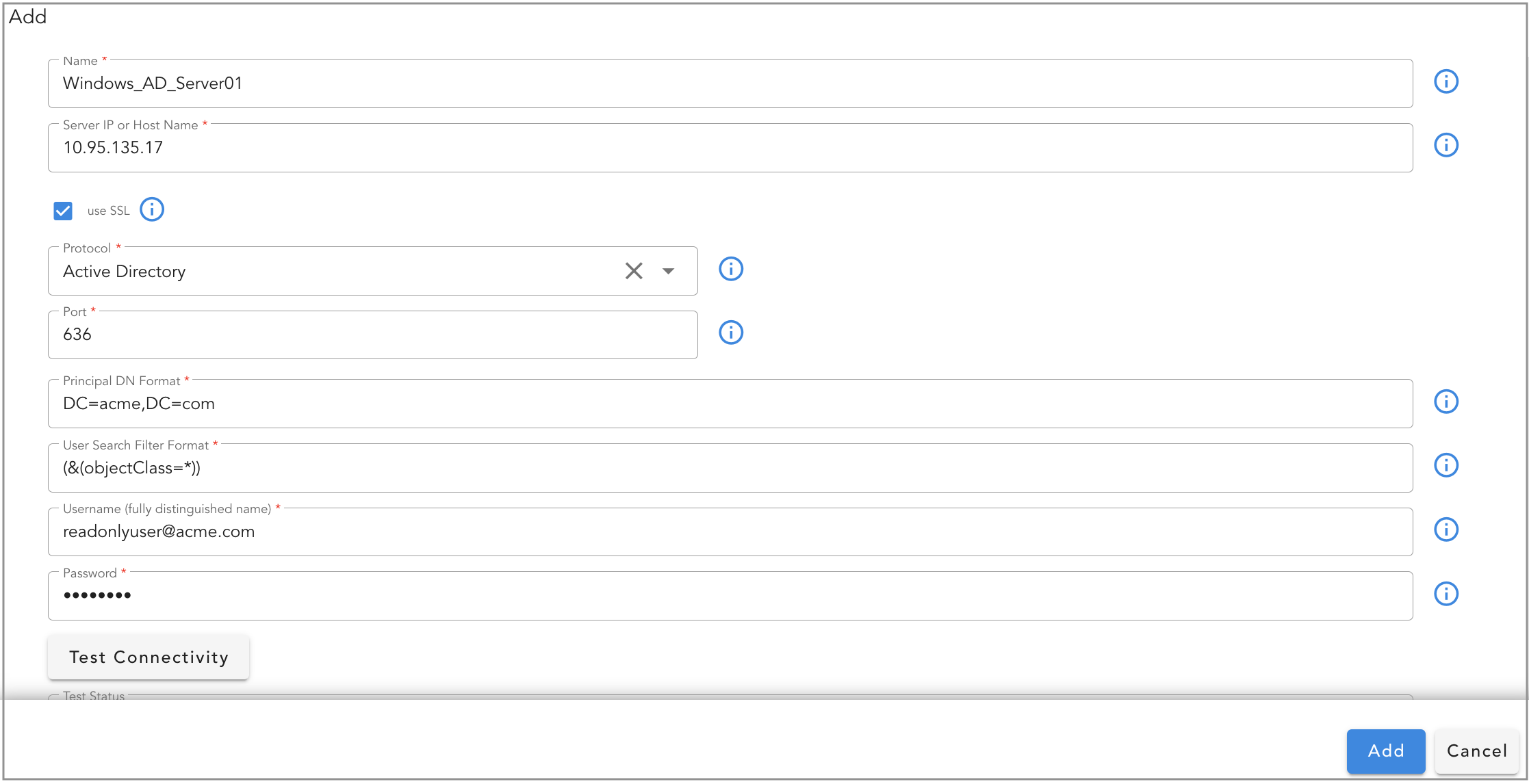
| Parameter Name | Description |
|---|---|
| Name | Specify a name or label for Windows Active Directory integration |
| Server IP or Host Name | Enter Active Directory server's IP Address or DNS Name |
| use SSL | Select this check box to use SSL protocol |
| Protocol | Select Active Directory |
| Port | Enter port 389 for non-SSL or port 636 for SSL protocol |
| Principal DN Format | Enter domain name in Distinguished Name (DN) format. For an example, if domain name is acme.com, DN format is DC=acme,DC=com. If domain name is dev.acme.com, DN format is DC=dev,DC=acme,DC=com |
| User Search Filter Format | Enter the value as (&(objectClass=*)). This filter is to include all Active Directory objects for searching the Users & Groups while importing them into RDA Fabric platform. |
| Username (fully distinguished name) | Enter a valid Active Directory domain user name in Distinguished Name (DN) format or in User Principal format (UPN). For an example, readonlyuser@acme.com is in UPN format which is acceptable. DN format for the same user is CN=readonlyuser,CN=Users,DC=acme,DC=com |
| Password | Enter User's password for the above specified domain user. |
Tip
Please note that only one Active Directory server integration can be added. After adding it successfully, the Add button will not appear in the UI. If a new Active Directory server needs to be added, either update the existing configuration or delete the current configuration and add a new one.
2.2.1 Import Active Directory Users
Tip
Before importing Active Directory users, it is a pre-requisite to create one or more Local User Groups and associate them to one of the available User Role.
Go to Main Menu --> Administration --> Users. Under User Groups section, click on Add Group action button to create a new user group.
Before importing Active Directory users, ensure that Active Directory user groups, to which the users belong, have been added.
Go to Main Menu --> Administration --> Authentication Servers --> User Groups
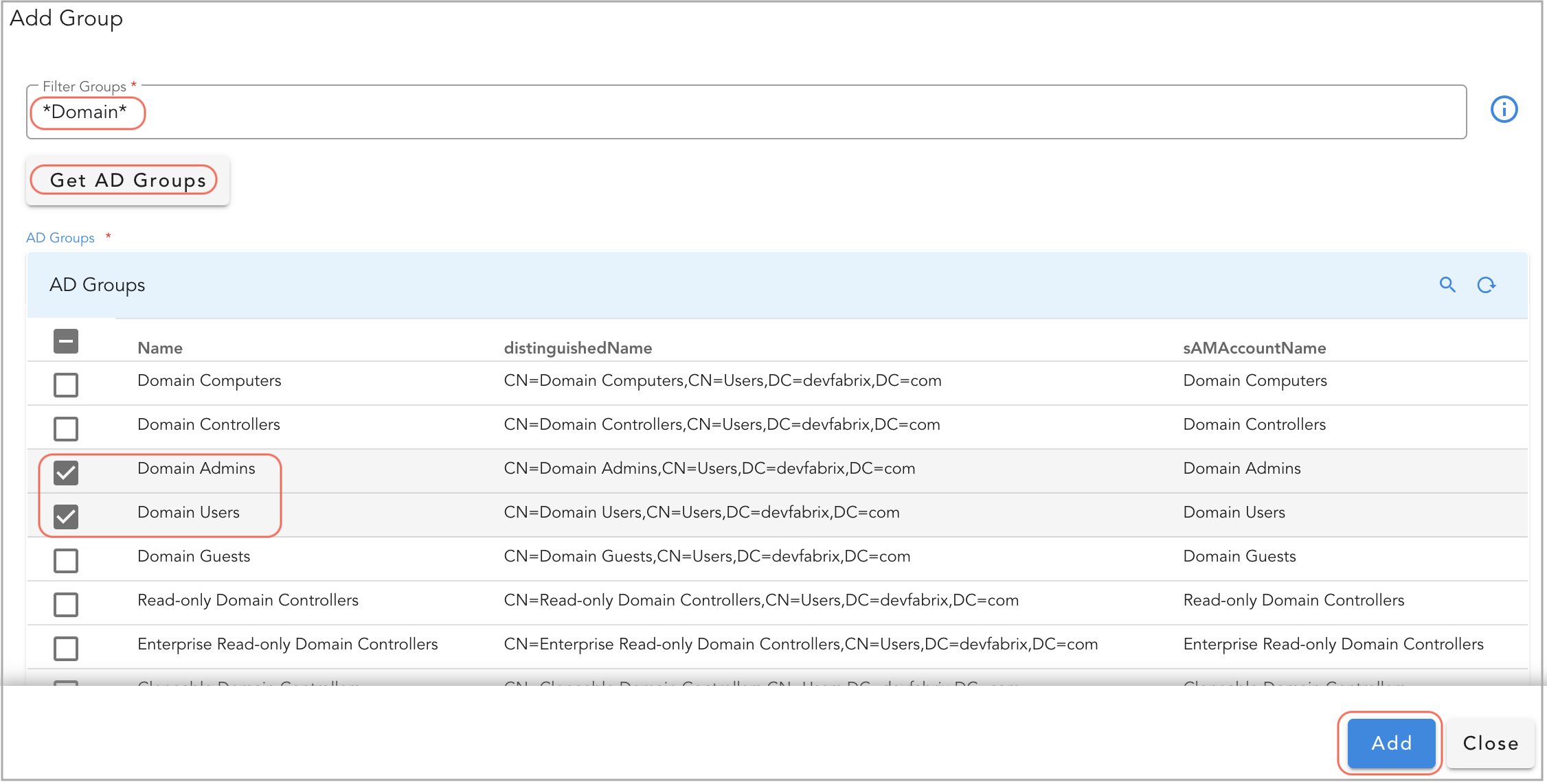
Click on Add Group button to search and import the Active Directory user groups.
In the pop-up window, under Filter Groups, enter *Domain* (as an example) and click on Get AD Groups
Select one or more User Groups from the list and click on Add button.
Tip
Searching for user groups in Active Directory supports the use of wildcards, such as '*' before and after a user group name. User group filter with a wildcard in the below screenshot is for a reference only.
To add the Active Directory users, click on Users section.
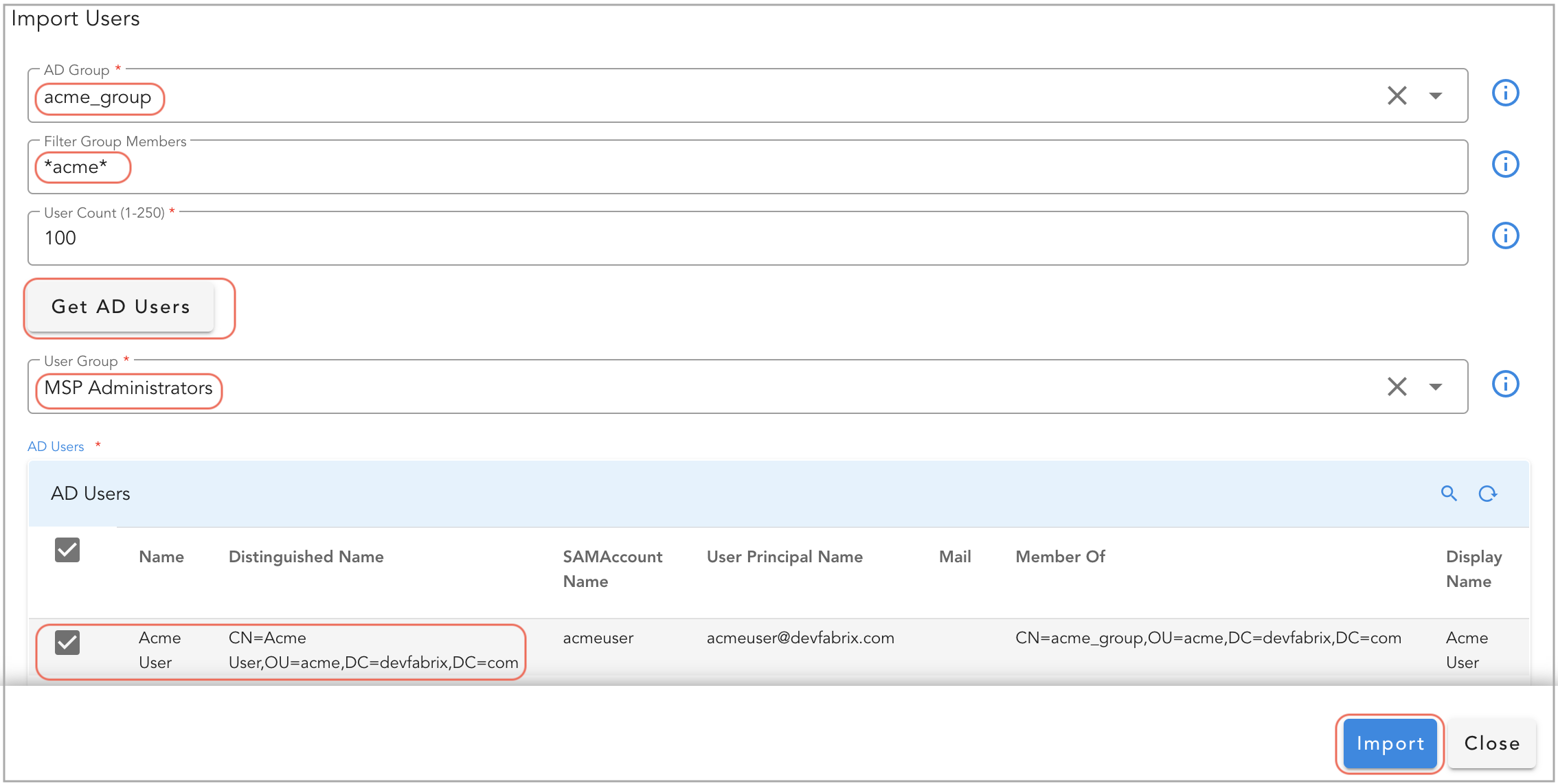
Click on Import Users button to add one or more Active Directory users.
In the pop-up window, below options are available.
-
From AD Groups: Select this option to list all of the imported Active Directory user groups in the above step. It allows to select one of the user group from which Active Directory Users can be imported. (Note: If the Users are part of Domain Users group, please select the below option instead.)
-
From AD Default Group: Select this option to import the users from default Active Directory group i.e. Domain Users
-
AD Group: Select one of the Active Directory group from the list. (Note: This option only available when From AD Groups option is selected above.)
-
Filter Group Members: Enter username string with a wildcard, such as
*acme*(as an example), and click on Get AD Users to retrieve a list of users that match the wildcard filter. -
User Count: The default value is 100, and the maximum supported value is 250. This value is set to limit the number of users to be imported from Active Directory.
-
User Group: Select Local User Group that was created with a User Role to associate one or more Active Directory users.
-
AD Users: Select one or more Active Directory users to be imported.
Click on Import button to import the Active Directory users.
Delete Imported Active Directory Users & User Groups:
Go to Main Menu --> Administration --> Authentication Servers --> User Groups or Users
Select User Group and from the action menu, click on Delete
Select User and from the action menu, click on Delete
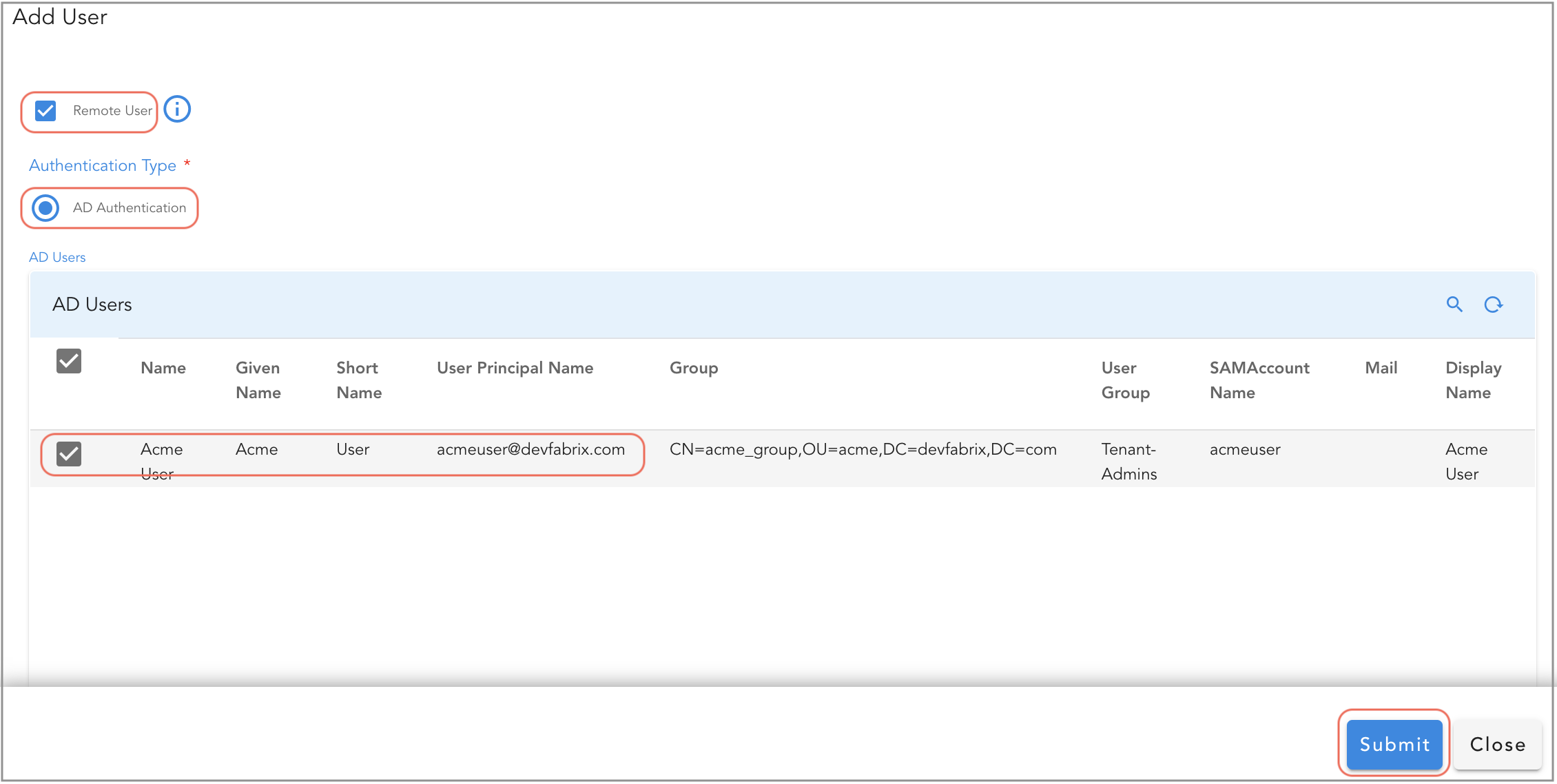
2.2.2 Add Active Directory Users
Go to Main Menu --> Administration --> Users
Click on Add User action button to add one or more Active Directory users.
Click on Remote User check box, under AD Users table, select one or more Active Directory users and click on Submit button.
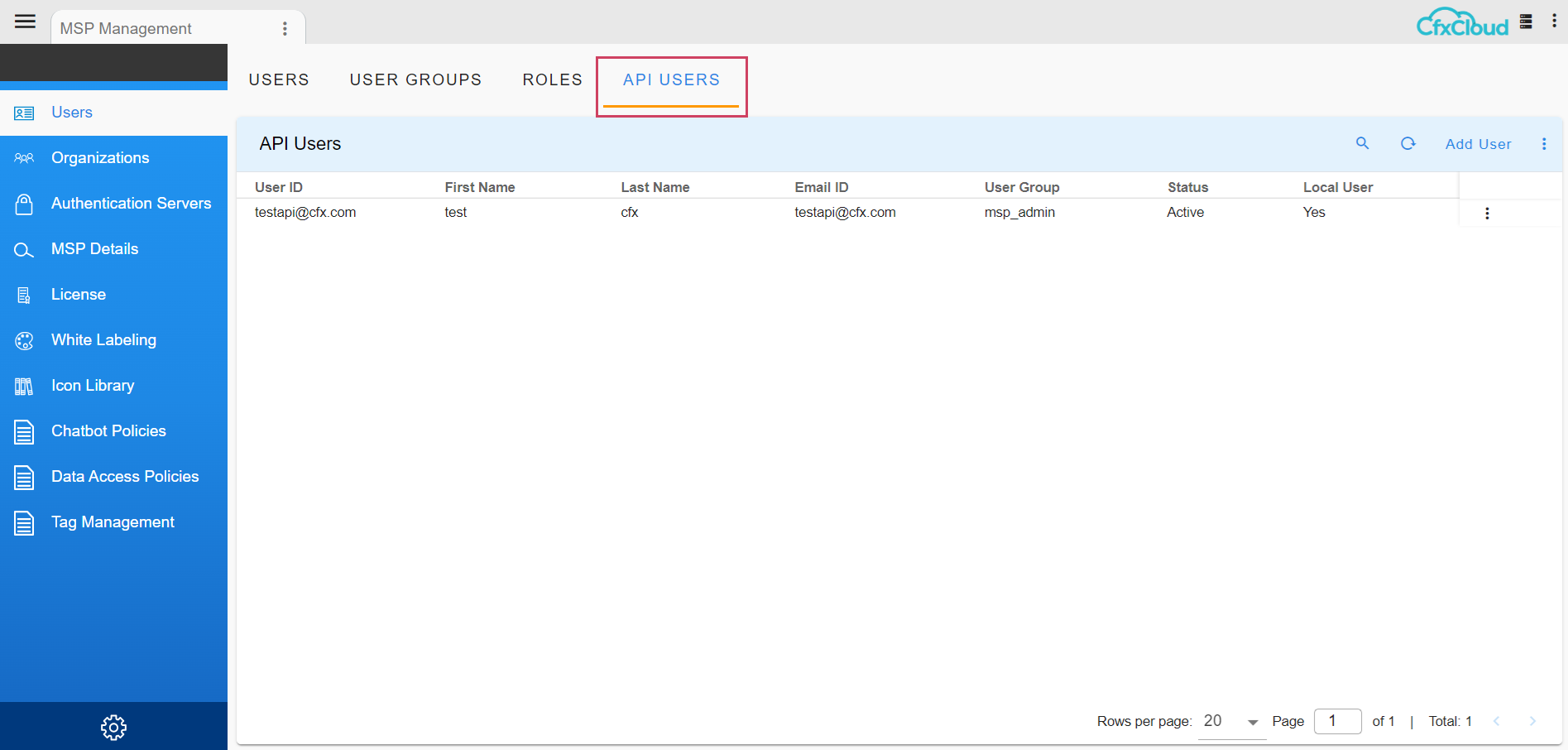
2.3 API Users
2.3.1 Onboarding API Users
-
On the Administration user's page, there is a New API Users Tab for users.
-
Navigation Path: Go to Homepage -> Administration -> Users
-
In order for API users to access the APIs in accordance with their roles, they will be assigned to a user group.
Click the Add user option to add new users.
- Users on-boarded through the API users report will only have access to the APIs. These users are restricted from logging into the portal.
MSP Admin users can also perform Deactivate, Delete, and Change Group actions on API User accounts.
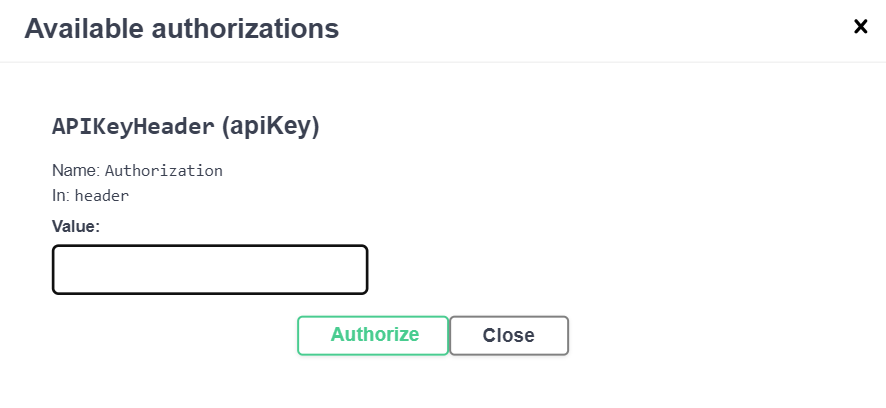
To Access Swagger APIs use the below mentioned URL
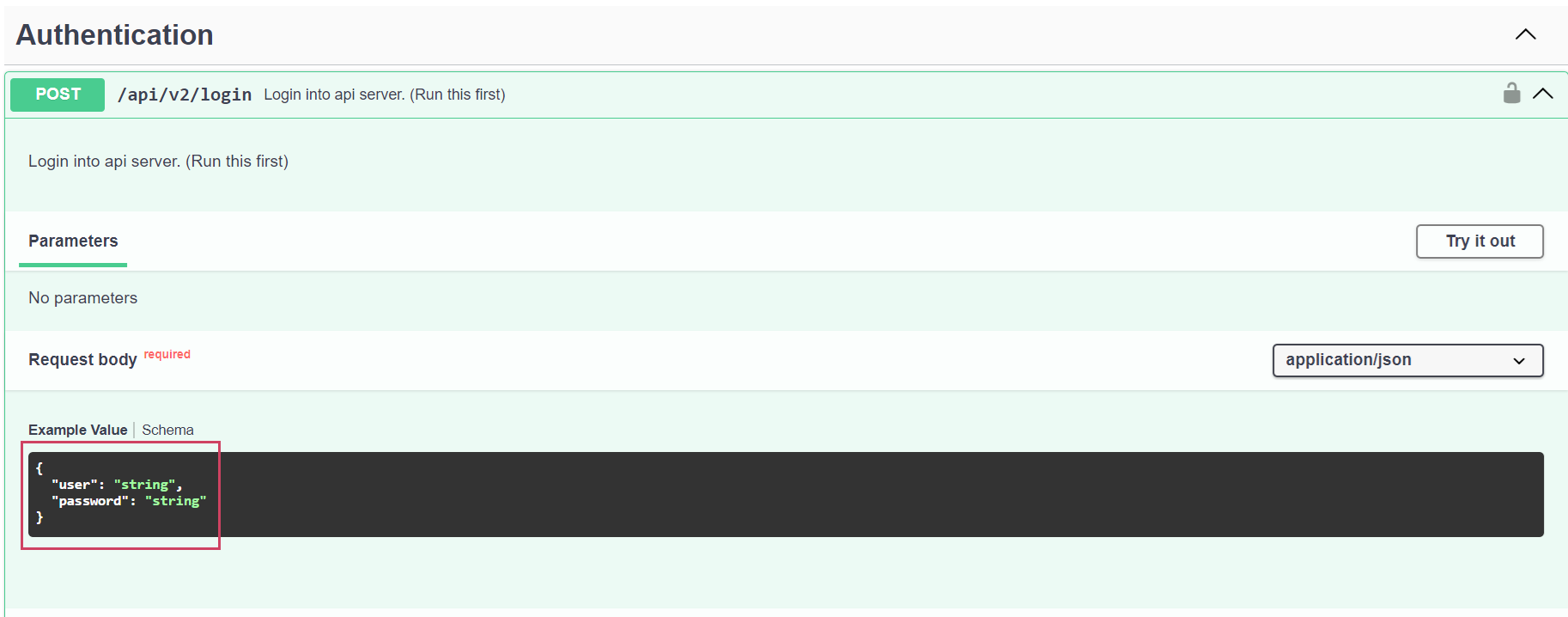
In Swagger APIs, there are two ways of authentication1. Using an Authorization Token
2. Using a User ID and Password
API users can authorize only using tokens and cannot use the user ID and password for login. Regular users can authorize using an authorization token or a user ID and password.
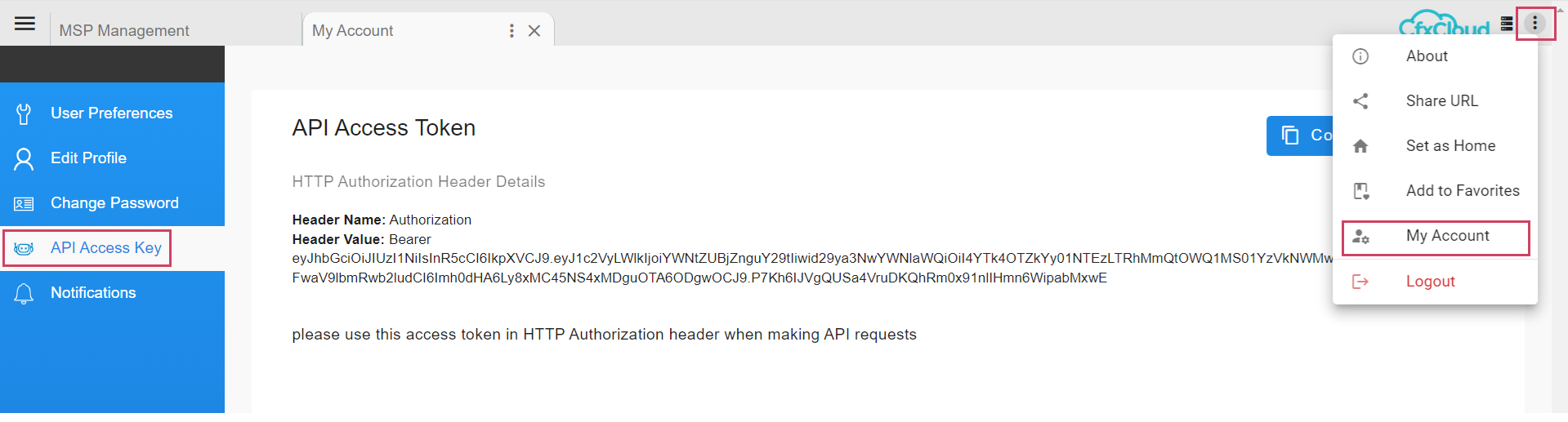
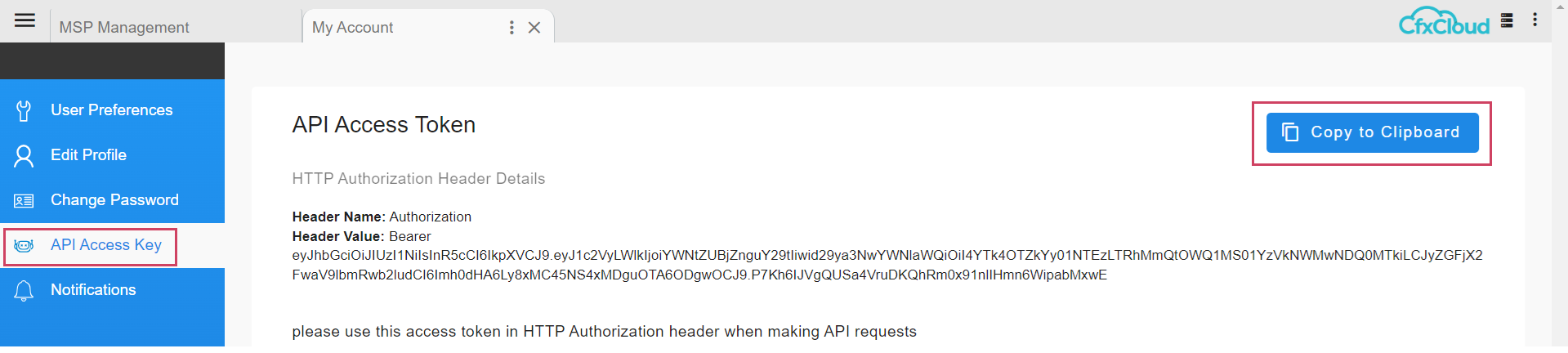
2.3.2 View Access Token
Navigation Path: Go to Homepage -> Administration -> Users -> API USERS -> View API Access Token
Admin users (MSP Admin) can generate the API Access token for each user using the row level action (View API Access Token) and share it with API users. Token can be copied using the Copy to Clipboard action as shown in the screenshots below.
Users can access API using the generated tokens
3. UI Management
3.1 Favorites
RDA Fabric platform allows users to set any user dashboards or administrative / configuration pages as Favorites
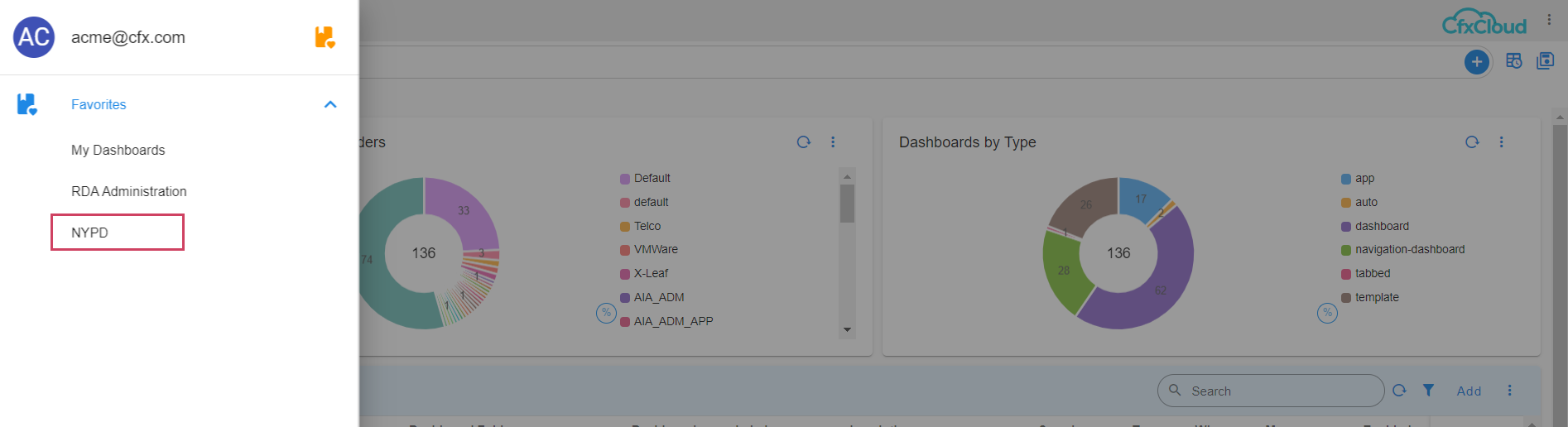
Select the desired tab which needs to be marked as Favorite
Click on the 3 Dot Menu select Add to Favorites
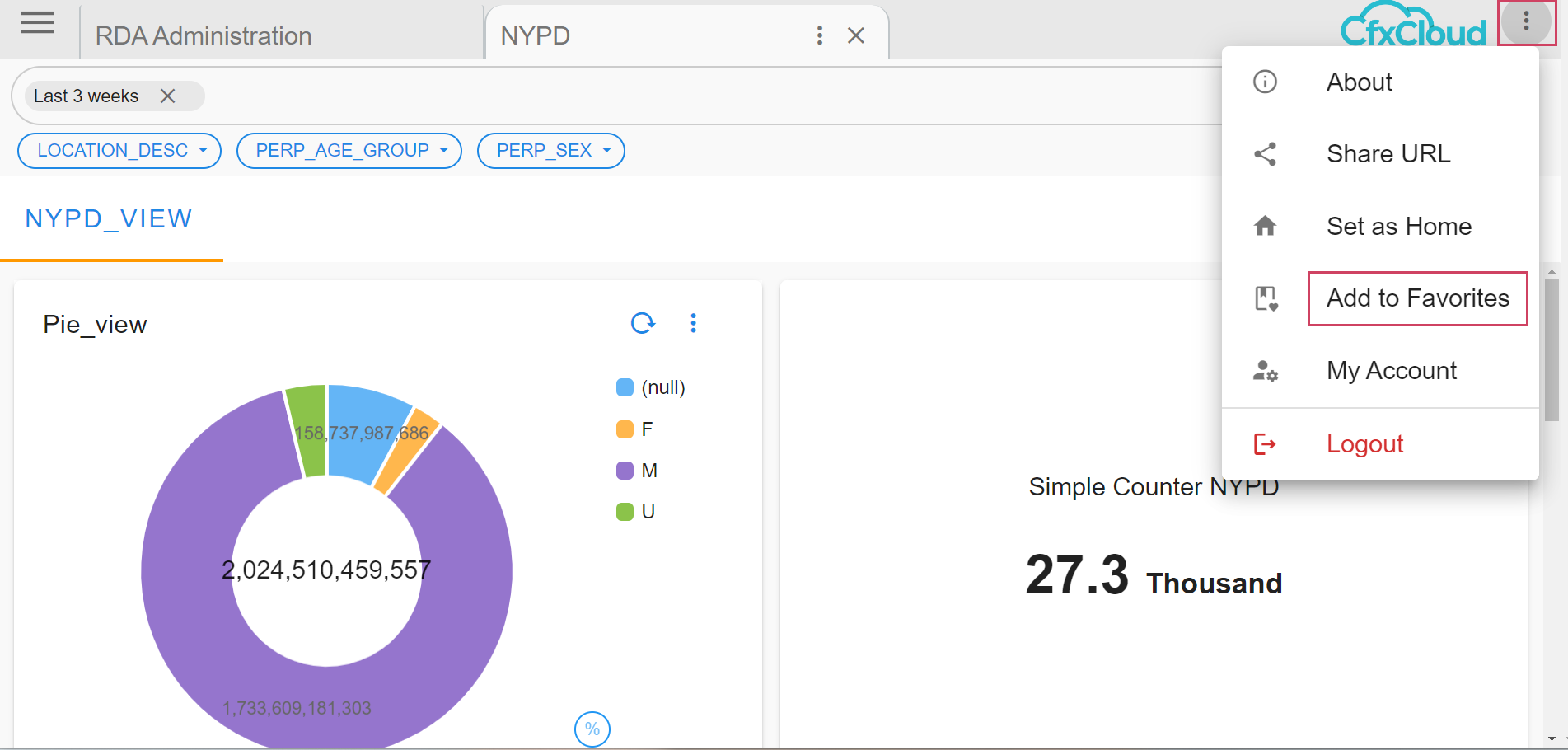
Then a Pop-up appears then we can change the label to the User Defined Label
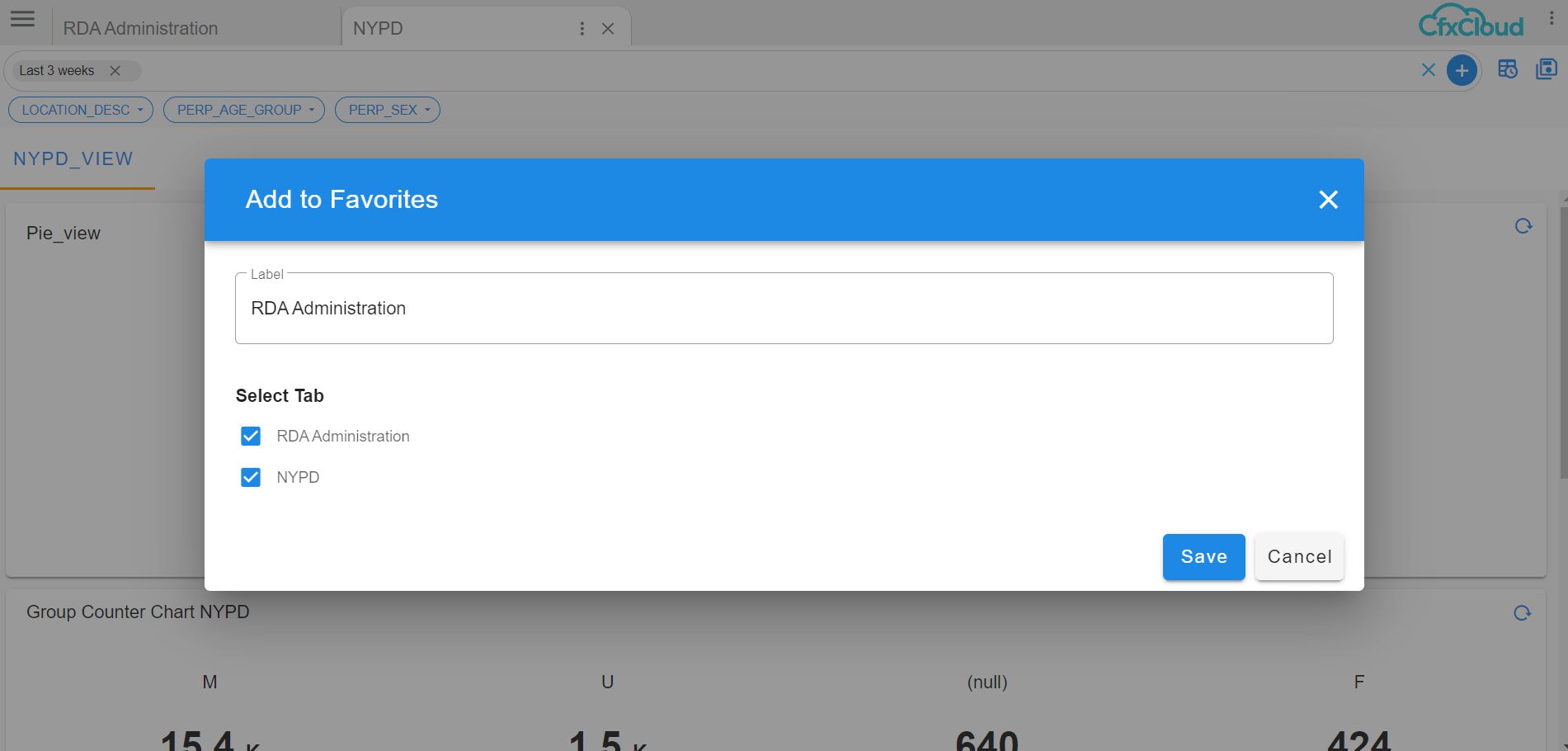
select the Tab that needs to be marked as favorite
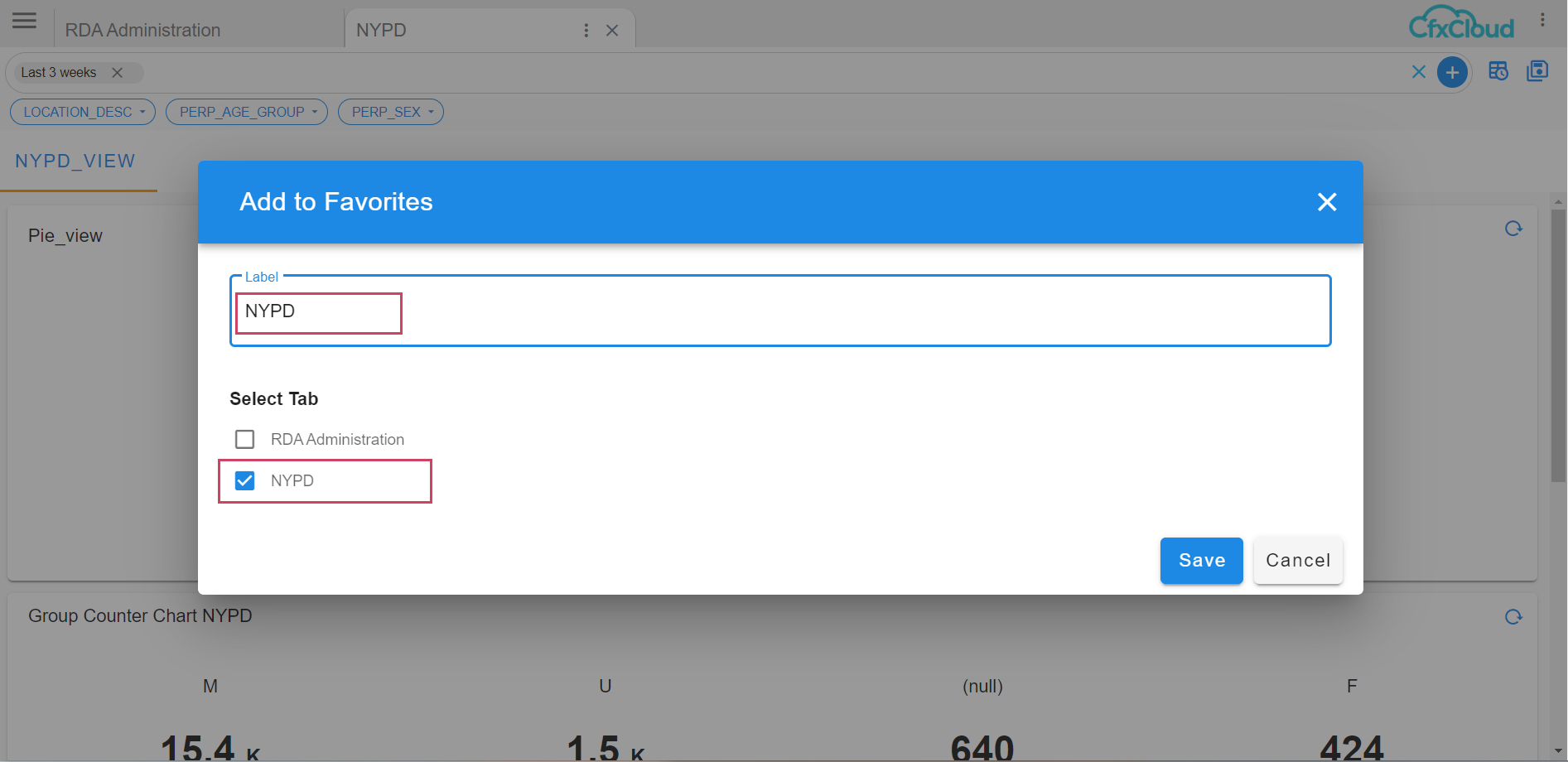
Click on the UI Menu and select Favorite Icon as shown below in the screenshot
Tip
Please click on the pictures below to enlarge and to go back to the page please click on the back arrow button on the top.
User needs to click on the icon as shown in the below screenshot
Now the user can see the Tabs which they have marked as Favorite, when the user clicks on it, user will get navigated to the respective dashboard
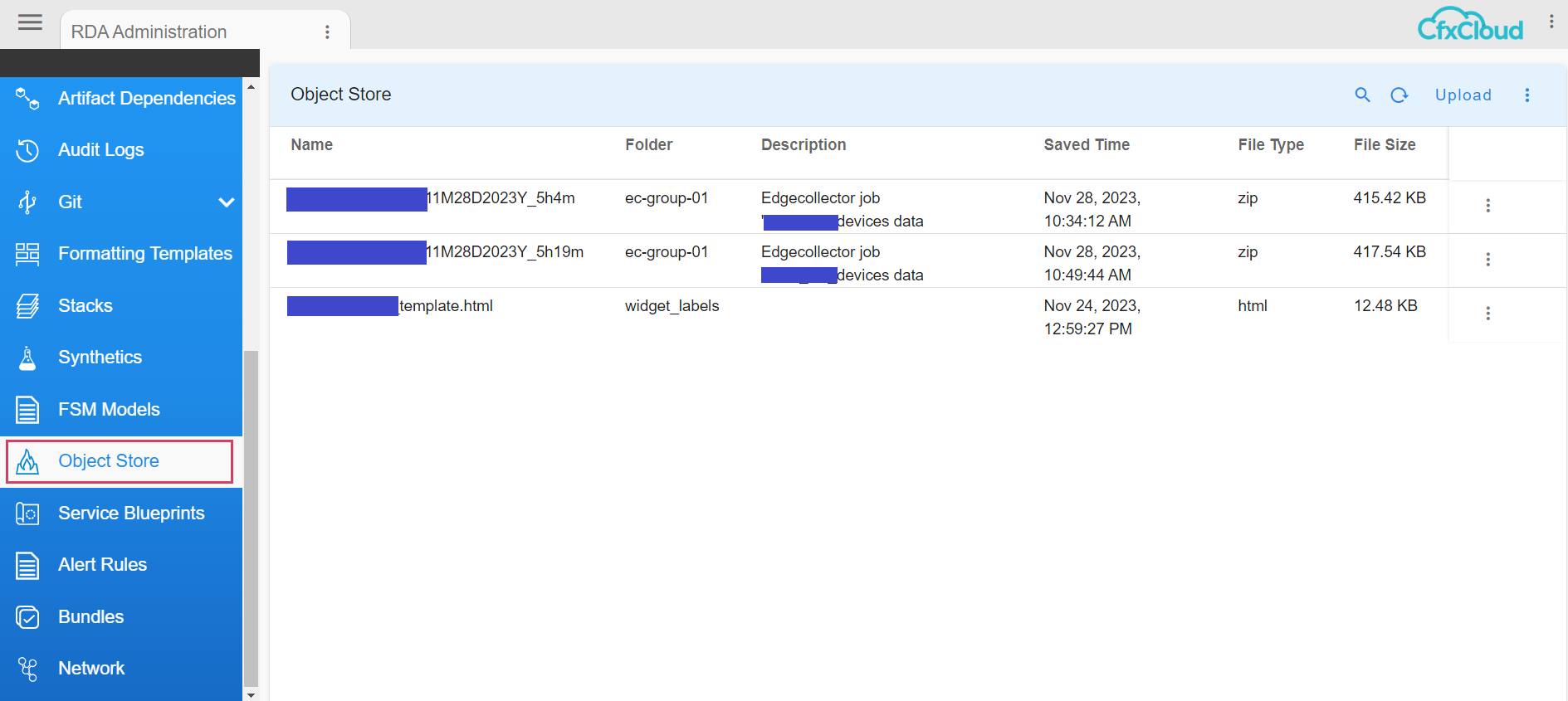
4. Object Store
RDA Fabric platform supports raw files to be added to object store by uploading from the CFX portal UI.
Object Store configuration is located at Menu → Configuration → RDA Administration → Object Store
4.1 Add Objects
Users can add Templates/Files. To add a new file to Object Store, click on Upload action
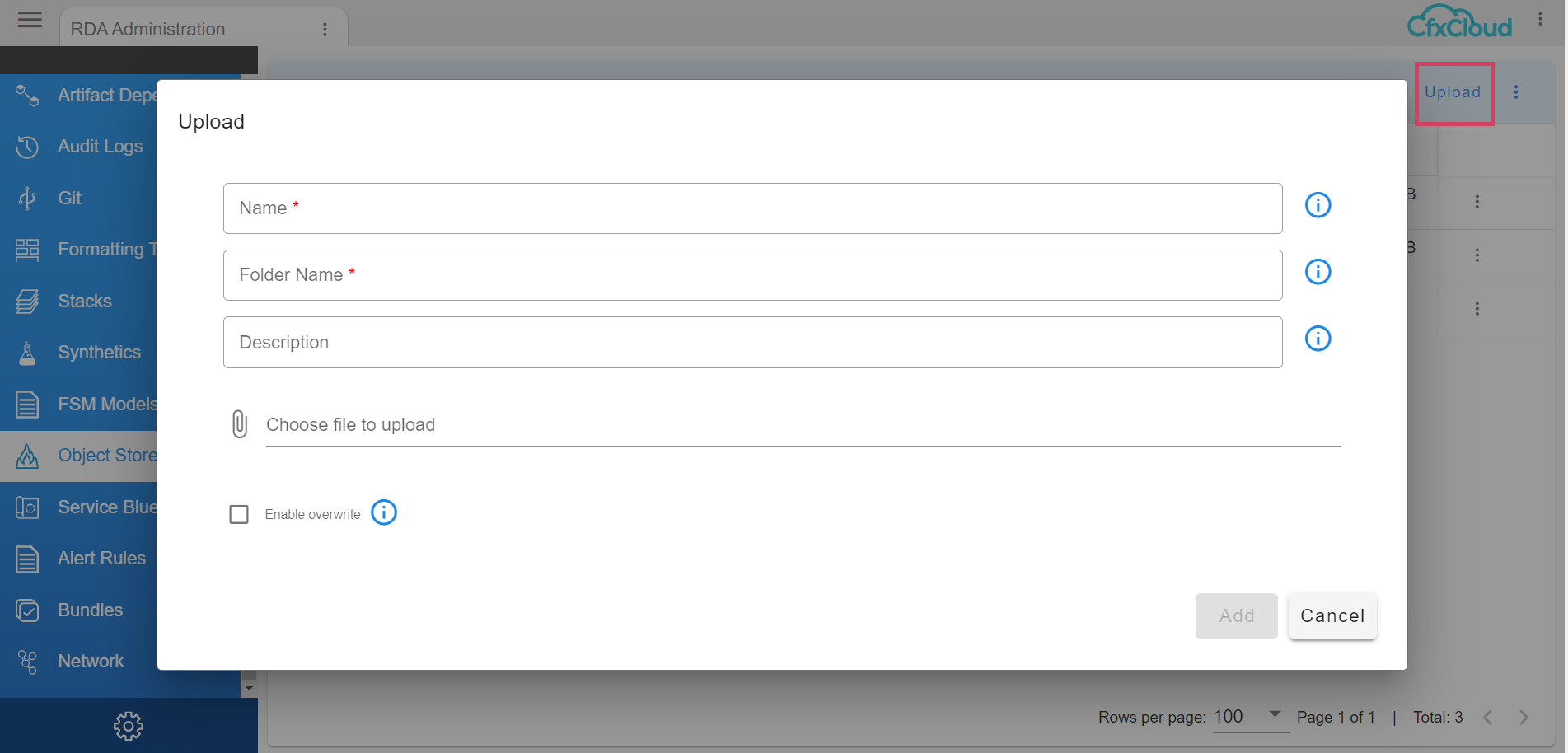
Provide a Name for the file and a Folder Name to upload the file, then click on the Add button to upload the file.
Supported File Types
File Types |
|
|---|---|
| csv | html |
| pqt | txt |
| parquet | zip |
| pa | gz |
| orc | tar |
| json | yml |
| xlsx |
Note
If you need to reupload any template that was already added or stored, click on Upload and provide the same inputs for Name, Folder Name, and upload the new file along with the selection of the checkbox Enable Overwrite. Then click on Save.
4.2 Object Management
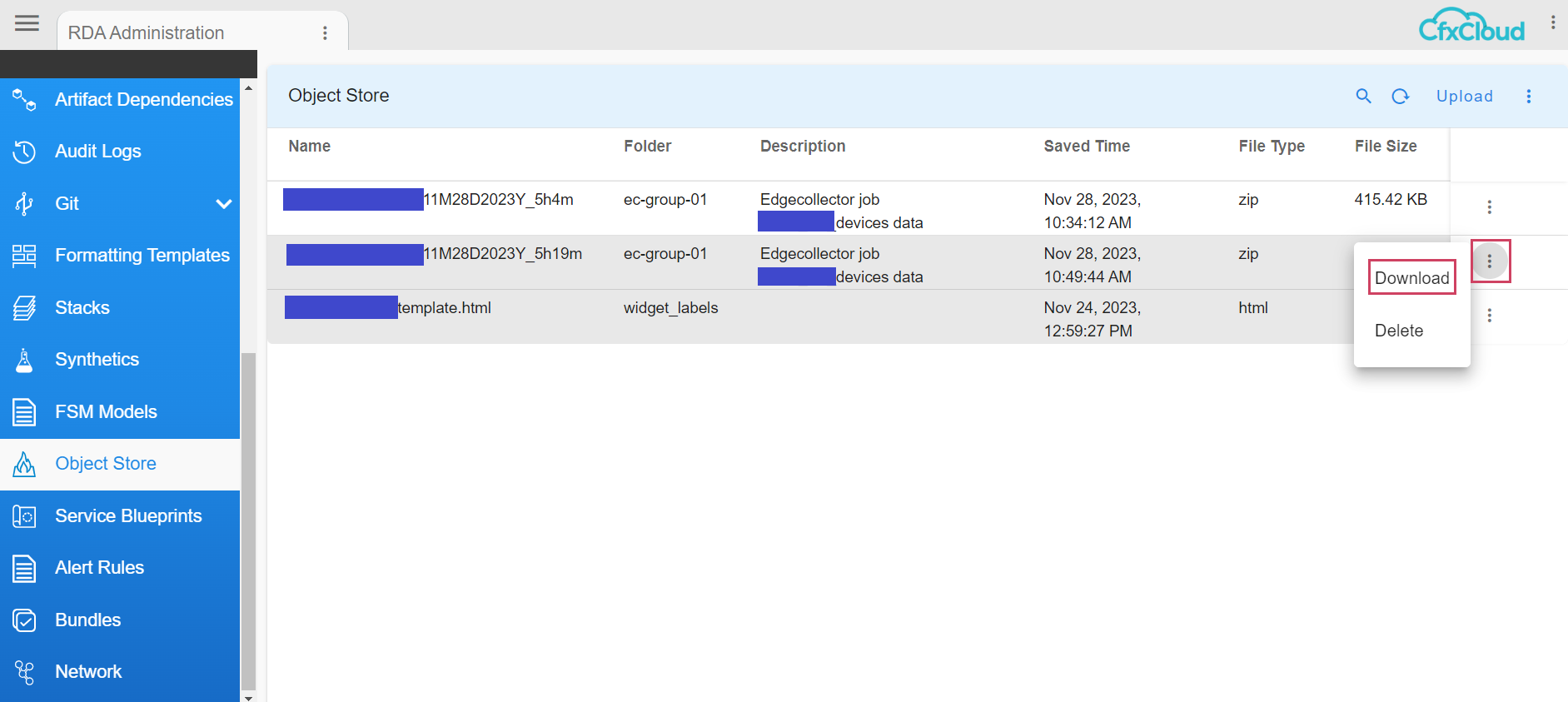
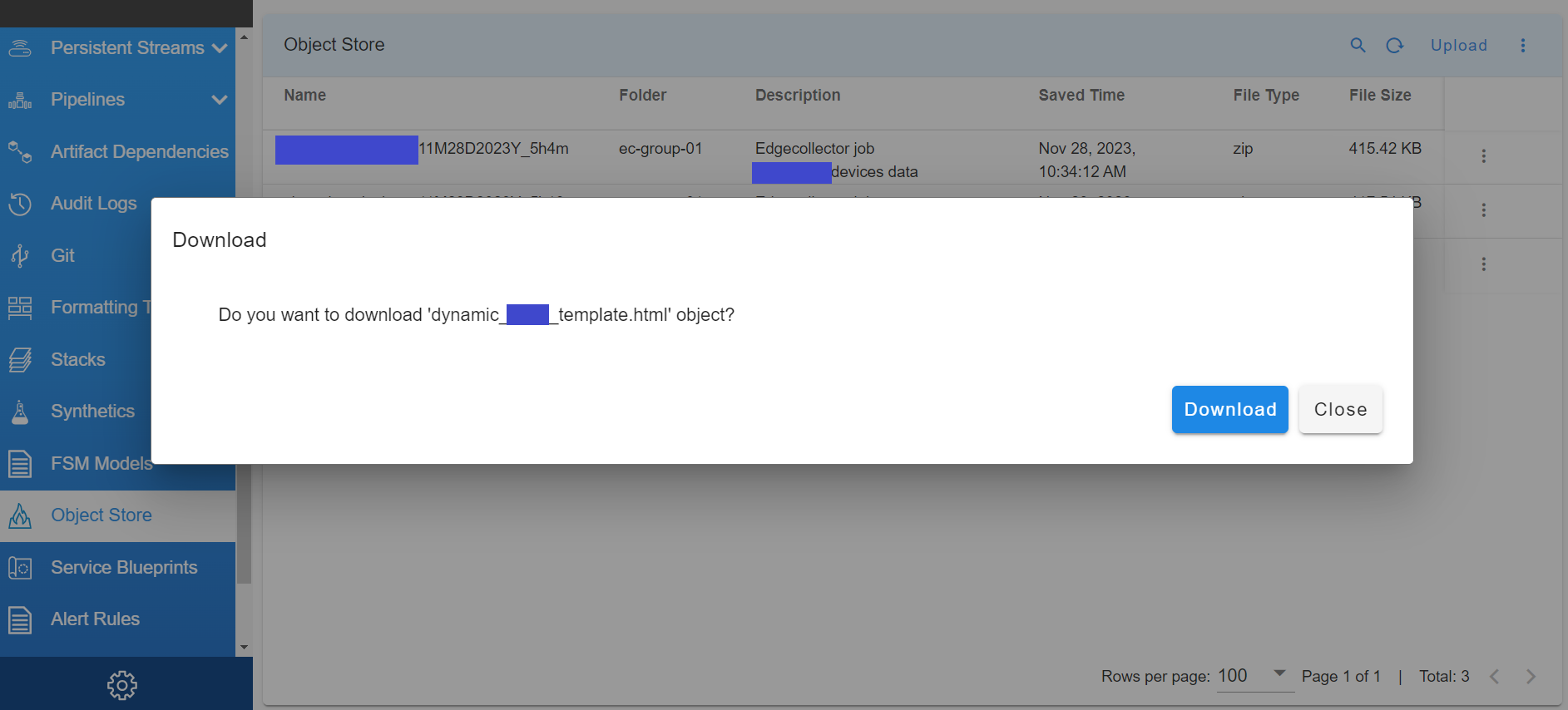
4.2.1 Download
- Allows to download the file that was uploaded earlier, The below Screenshots show how thats going to look like
Tip
Please click on the pictures below to enlarge and to go back to the page please click on the back arrow button on the top.
When the user clicks on to Download this is how its going to look like in the below screenshot.
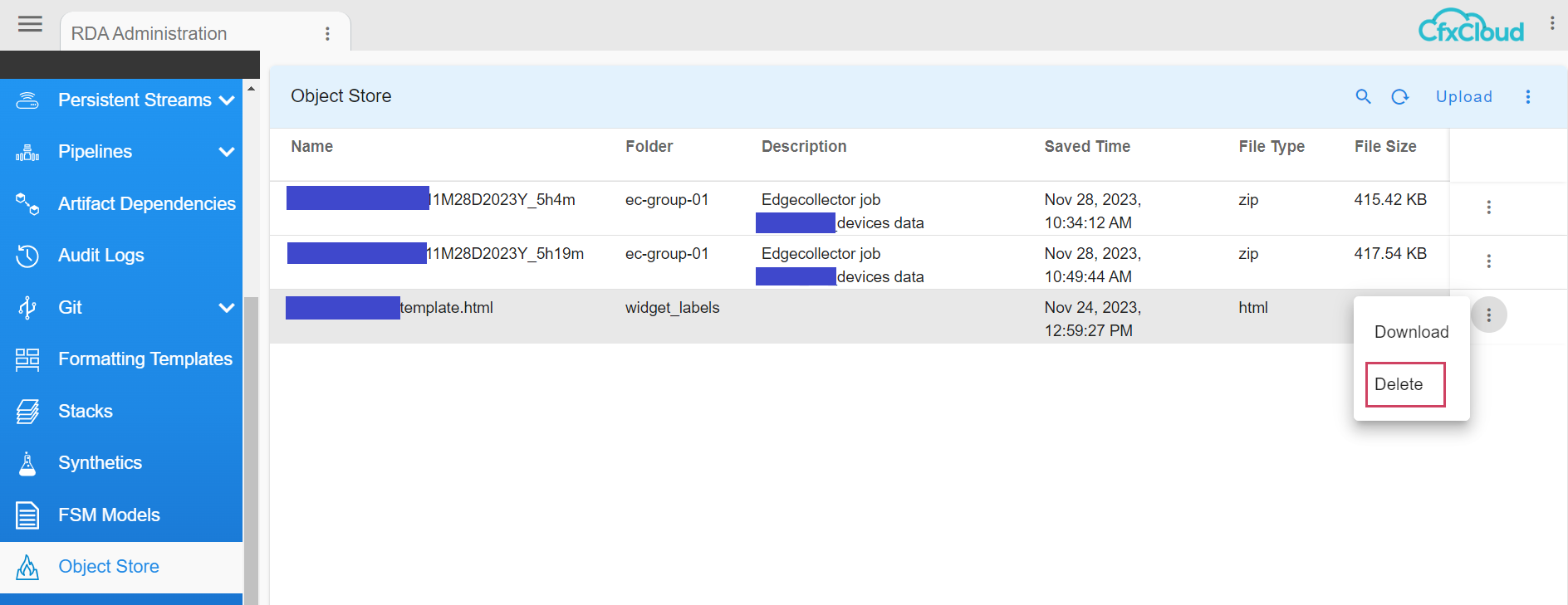
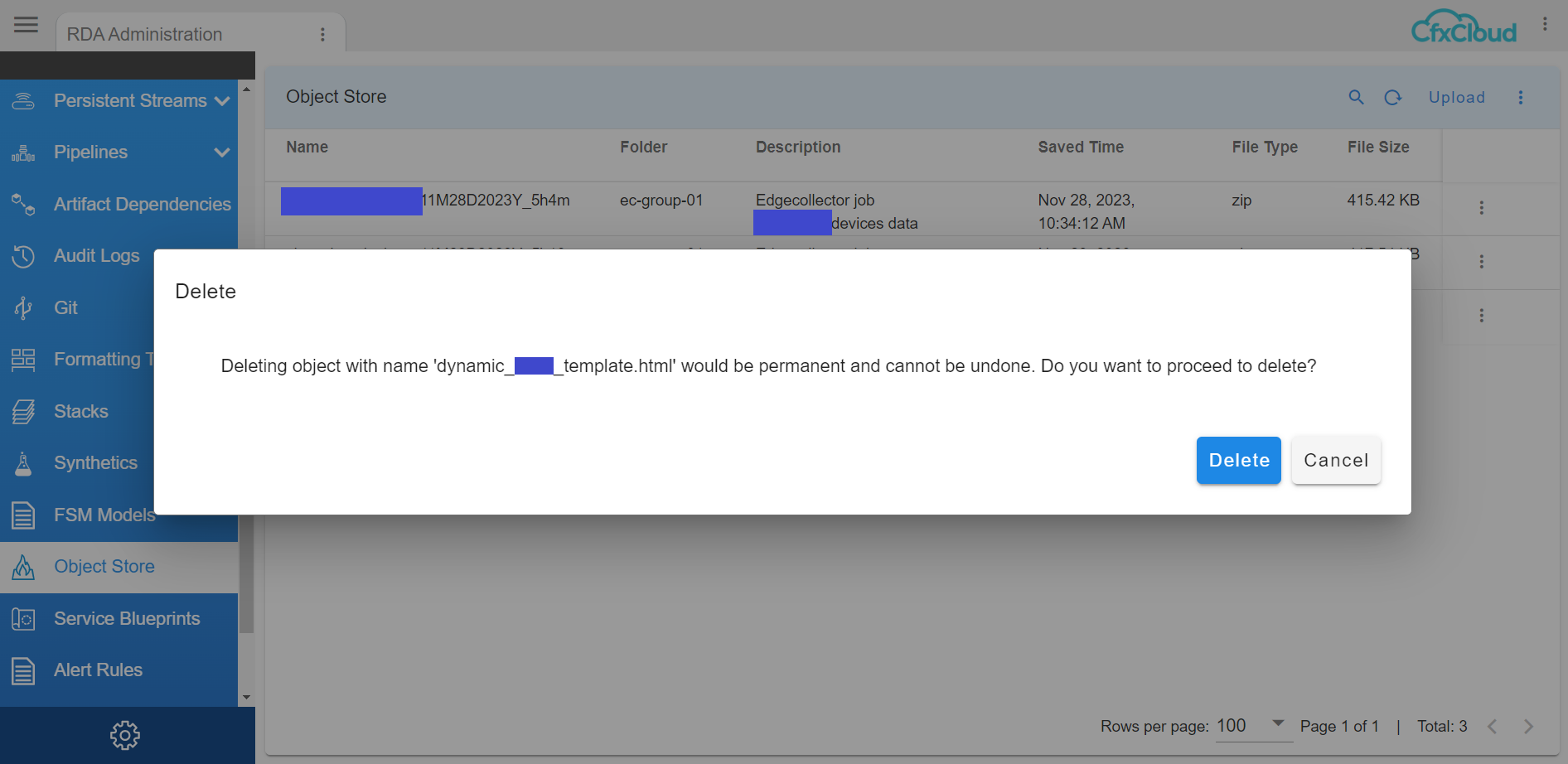
4.2.2 Delete
- This option allows the user to delete the files that were added earlier as shown in the below screenshot.
When the user clicks on to Delete this is how its going to look like in the below screenshot.
5. Pstream Data Archival
Data retention supports the ability to backup the data and store it in storage object. It is supported to take backup automatically on a daily basis if archival is enabled on the data.
5.1 Enabling Data Archival
After login into CFX Portal UI go to Menu → Configuration → RDA Administration → Persistent Streams → Click Persistent Streams
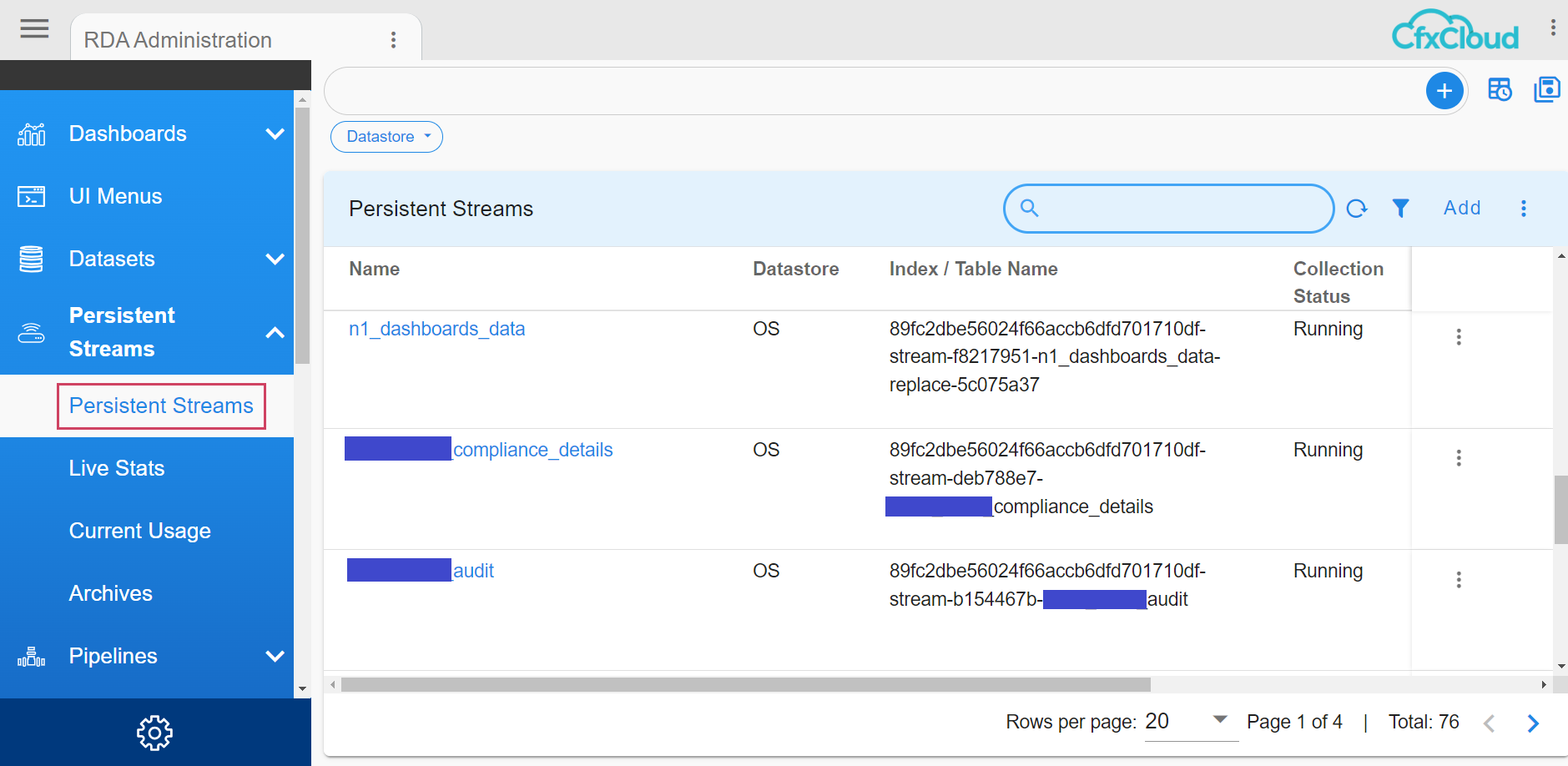
Feature can also be enabled by passing a flag to a pstream while adding/editing the pstream.
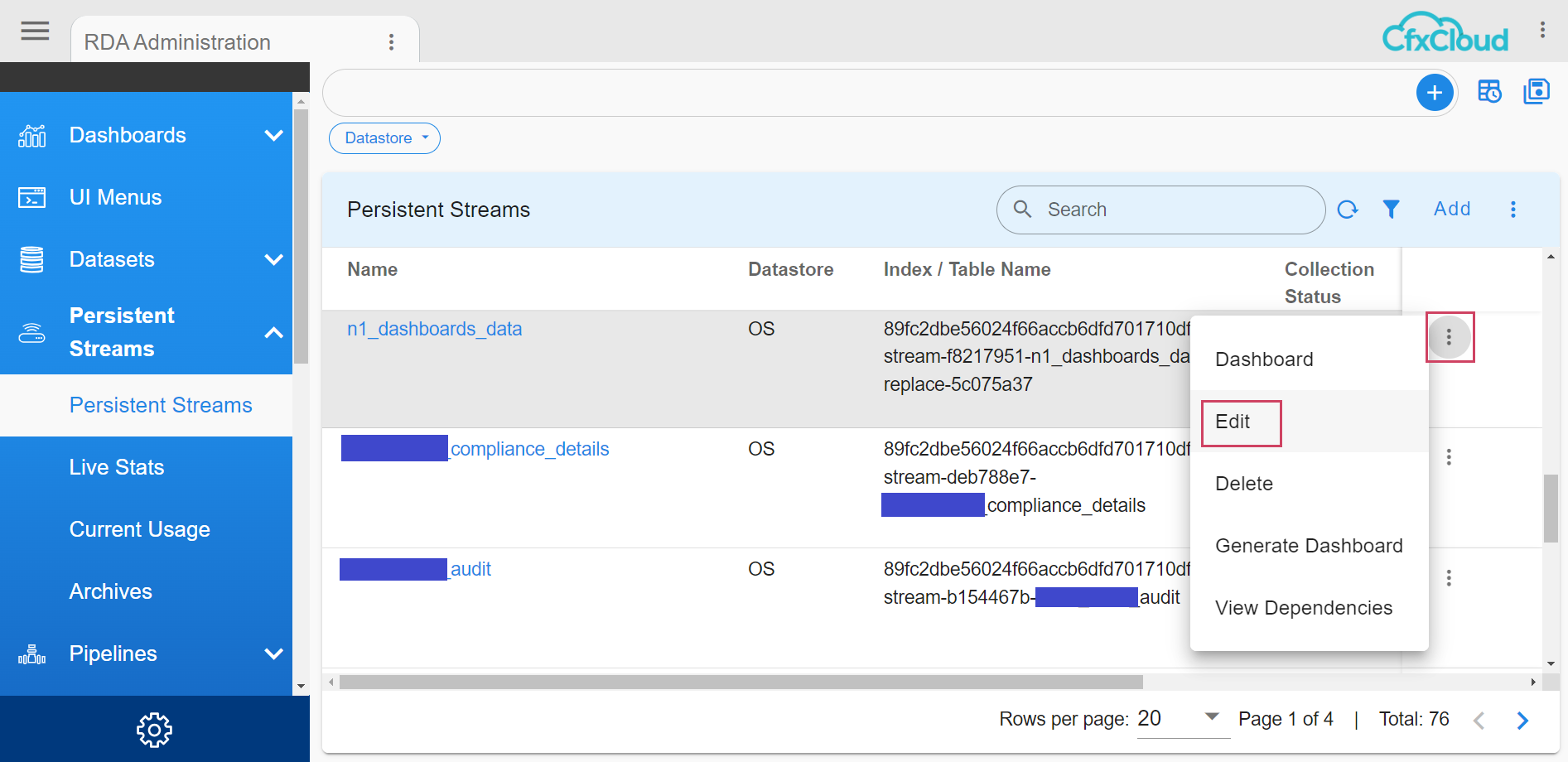
Adding/Editing the required pstream
Parameter Name |
Mandatory | Description |
|---|---|---|
max_age_in_days |
no | Specify the number (days) after which the prior archived data is automatically deleted from the object storage. |
frequency |
no | Based on the specified interval, data is backed up. We currently only support daily. |
Note
When data collection happens for the first time it takes backup for the last 7 days.
5.2 Backup Collection
Daily Backup is configured to collect at 12AM UTC Time.
5.3 Backup Status
Once we have archival enabled for a pstream as it takes a backup, check if the backup is successful and once backup is successful users can see all the backups in CFX UI in the Archives page
Once we have archival enabled for a pstream as it takes a backup and once backup is successful users can see all the backups in CFX UI in the Archives page.
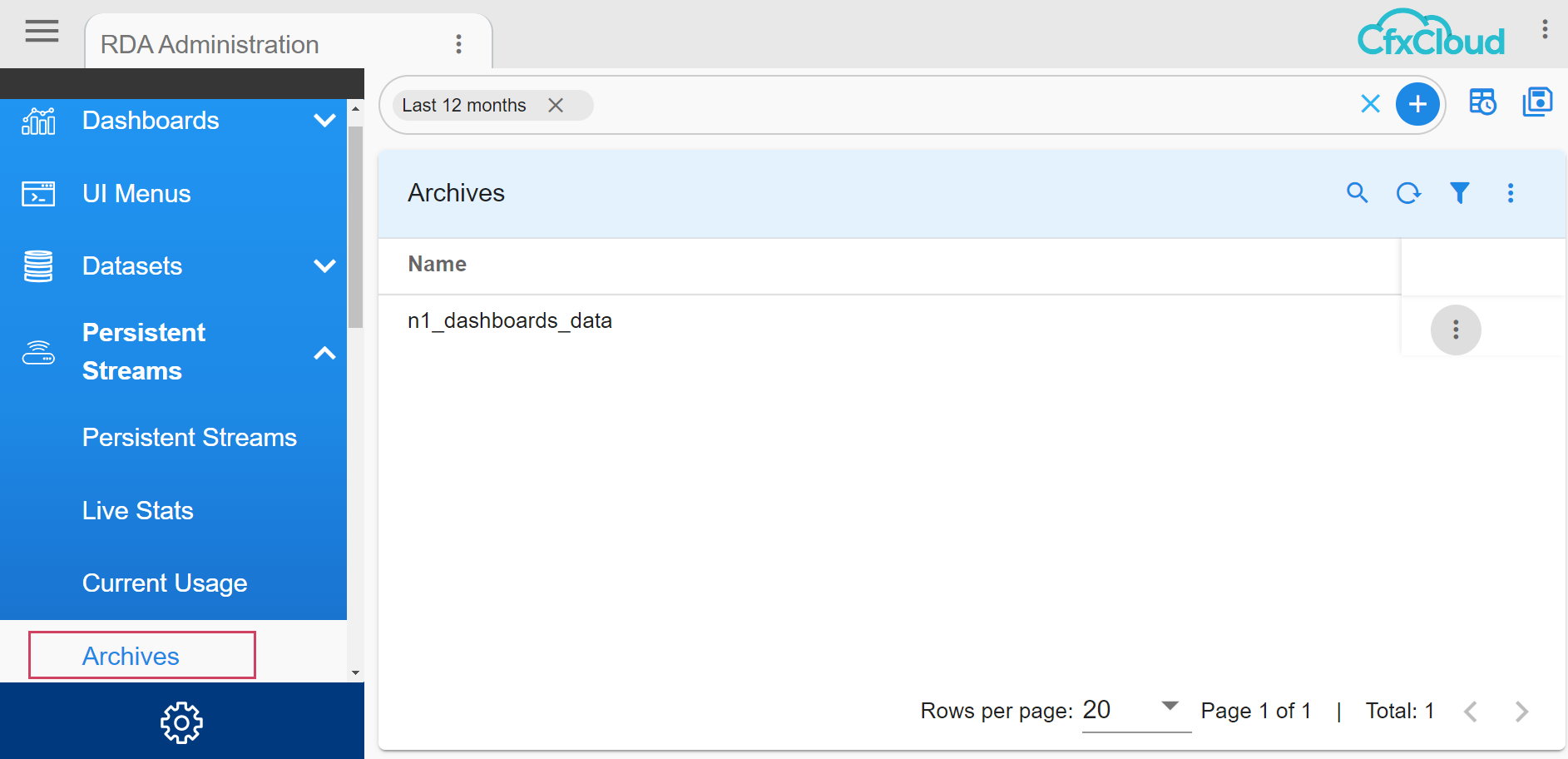
5.4 Download Archived Backups
All the successful backups collected/stored will be shown in the Archives page with the name of pstream(s). Click on the action of “View Archives” for a specific pstream user need to download the backup data.
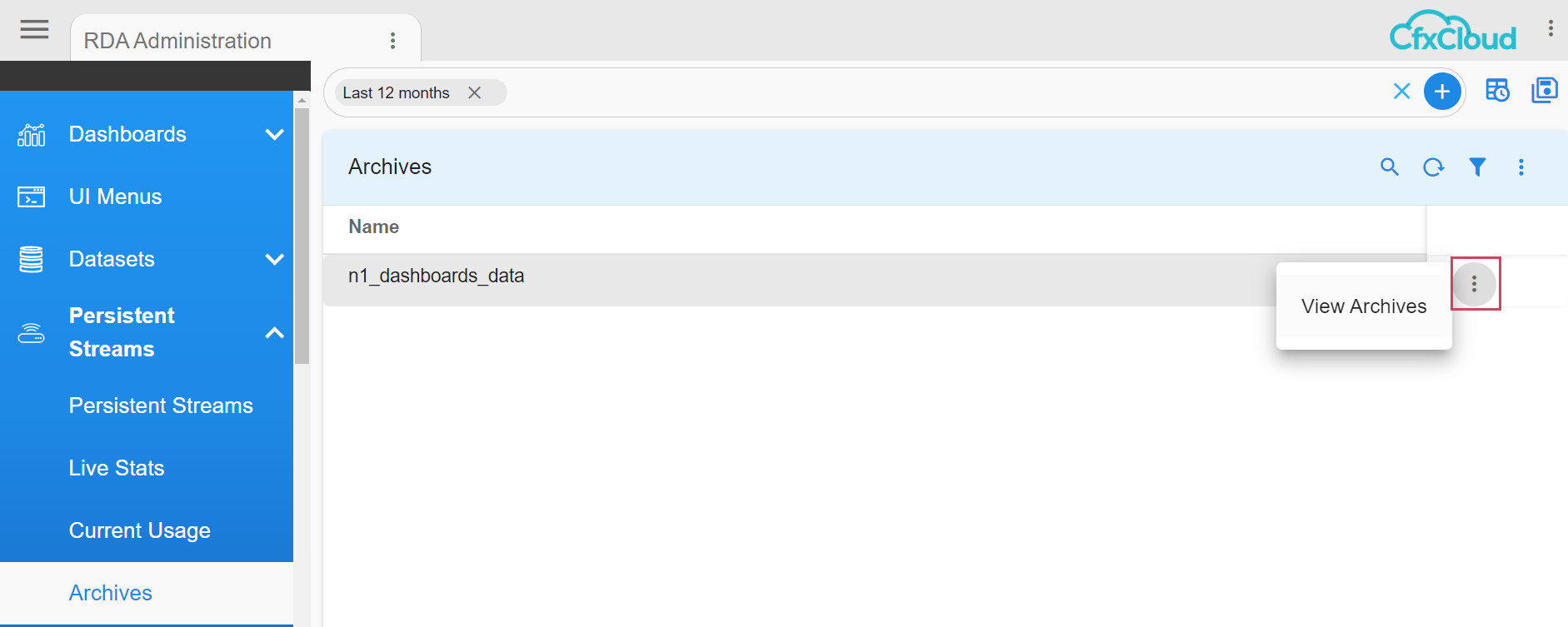
Note
Download action gets enabled only when backup data has any update in the last 24 hours (daily schedule). If there is no update in data in the last 24 hours the action will not get enabled
5.5 Backup Data Transfer
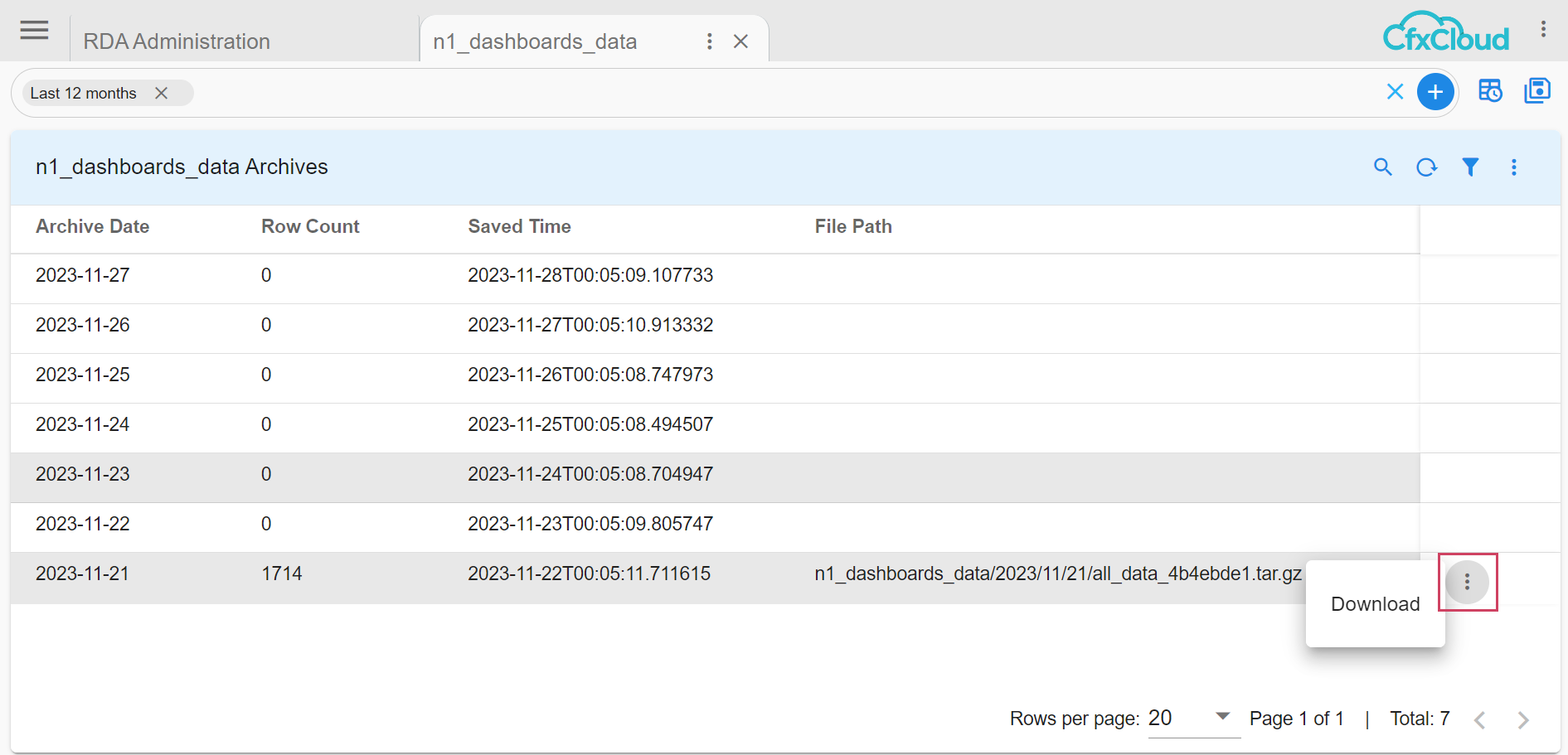
Can a user transfer the downloaded, backed up data to a different setup? Yes, Once the file is downloaded, user will see a file named
pstreamName_dateofbackup_time tar.gz downloaded
n1_dashboards_data/2023/11/21/all_data_4b4ebde1.tar.gz
CFX supports multiple ways to Dump/Transfer backed up data to different setup
5.6 Ingest the Backup data to Pstream
-
As the file is downloaded on your computer you need to extract the
<backupfile>.tar.gzusing standard ‘gunzip’ or other utility. Once the file is extracted, user will see tmp folder in the same location. -
In tmp folder, user will see a file name
<tmp***>.gz, user is expected to to extract the gz file as well using gunzip or standard utility, Once extracted, user will see<tmp***>file -
As the extracted file will not have proper file extension, it will be saved as a document. Users can rename the file with extension as .csv. Ex:
<tmp***>.csv -
Login to CFX UI go to Menu → Configuration → RDA Administration → Persistent Streams → Click Persistent Streams and add the dataset using csv file. Click on Persistent Streams (below datasets) and make sure the new stream is present where the data needs to be copied or imported. If a stream is not present, create a new stream.
-
Click on Datasets (Page above to persistent streams) → Click Datasets and add the dataset using the csv file extracted in the earlier step.
-
On the new dataset that is created click on the action menu and select Ingest to Stream and select the stream name in the pop-up and click on Ingest. Users can check the status of data ingestion in rda_system_collector_ingestion_job_status in persistent streams report.
-
Data will be shown in the stream once data is ingested successfully to pstream.
Note
Timestamp date in pstream will be shown with the date that the backup has taken and with default time filter of Last 24 Hours data will not be shown in the pstream.
5.7 Using RDAC Commands
-
Copy the downloaded file to one of the VM where rdac is running.
-
Extract the file using below commands.
#tar -xvf <pstreamName_dateofbackup_time>tar.gz
#cd tmp/
#gunzip <tmp***>.gz
#mv <tmp***> <tmp***>.csv
-
Login to CFX UI go to Menu → Configuration → RDA Administration → Persistent Streams → Click “Persistent Streams” and add the dataset using csv file. Click on the Persistent Streams (below datasets) and make sure the new stream is present where the data needs to be copied. If a stream is not present, create a new stream.
-
Using rdac we can copy the data to pstream using the below command.
Below is the terminal output if data gets copied to stream.
Reading input data file...
Input data file has 1714 Rows and 62 Columns
Publishing 1000 rows..
Publishing 714 rows..
Completed loading of 1714 rows into stream demo_data in 1.3 seconds
6. Tag Management
-
Basic functionality of tags is to filter data displayed within dashboards dynamically
-
Only user with MSP Administrator role can tag artifacts
-
Artifacts that support tags:
a) Dashboards
b) Datasets
c) PStreams
d) Credentials
-
All users belonging to a user group with specific tag(s) when they login they see only the artifacts with those particular tag(s)
-
Example: If a User Group is assigned Tag Acme, all the users in that user group when they login will see only the filtered artifacts that have Tag Acme.
-
Users with msp-admin or workspace-admin role can see all the artifacts
Tip
Please click on the pictures below to enlarge and to go back to the page please click on the back arrow button on the top.
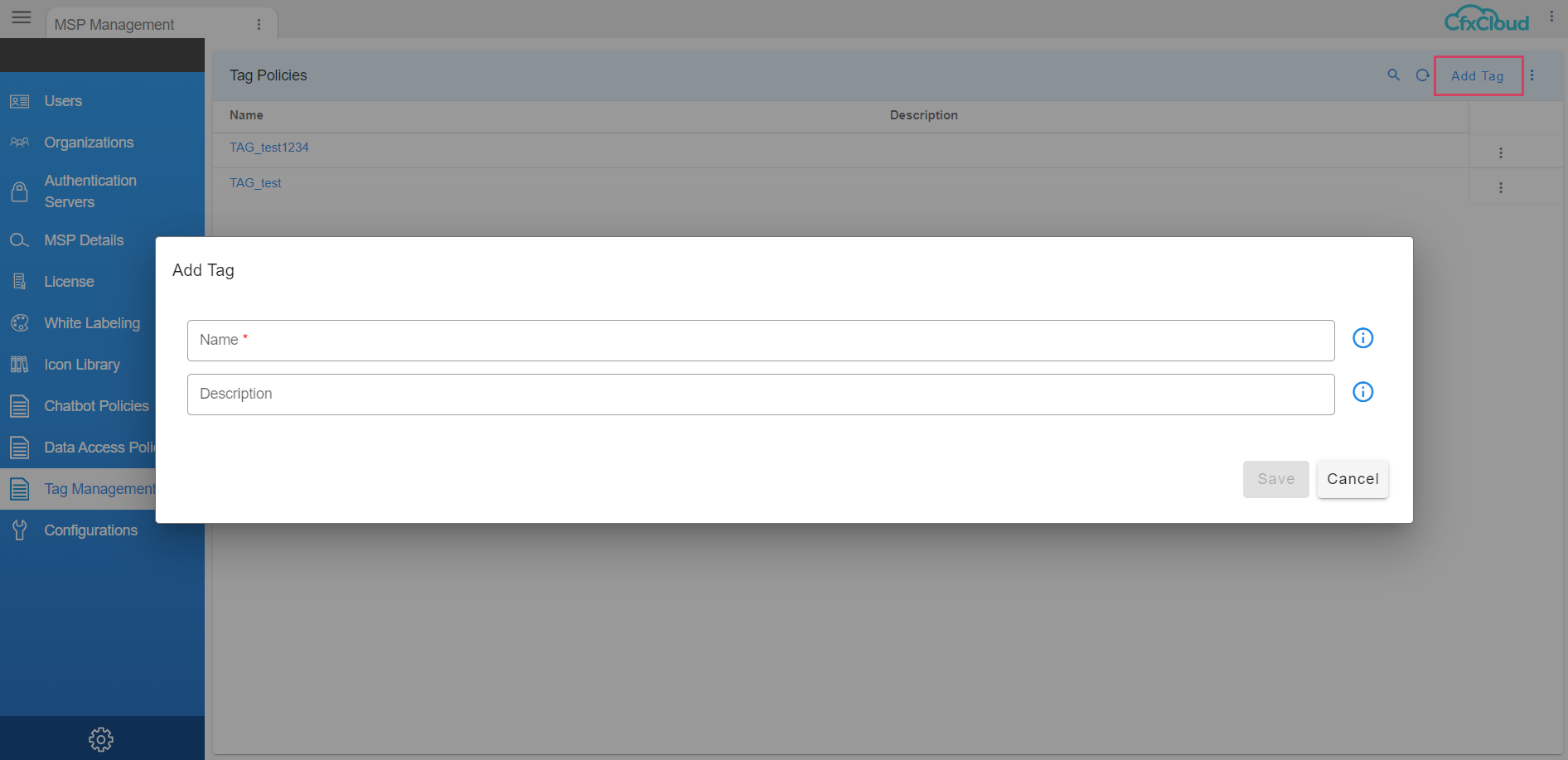
6.1 Add Tag
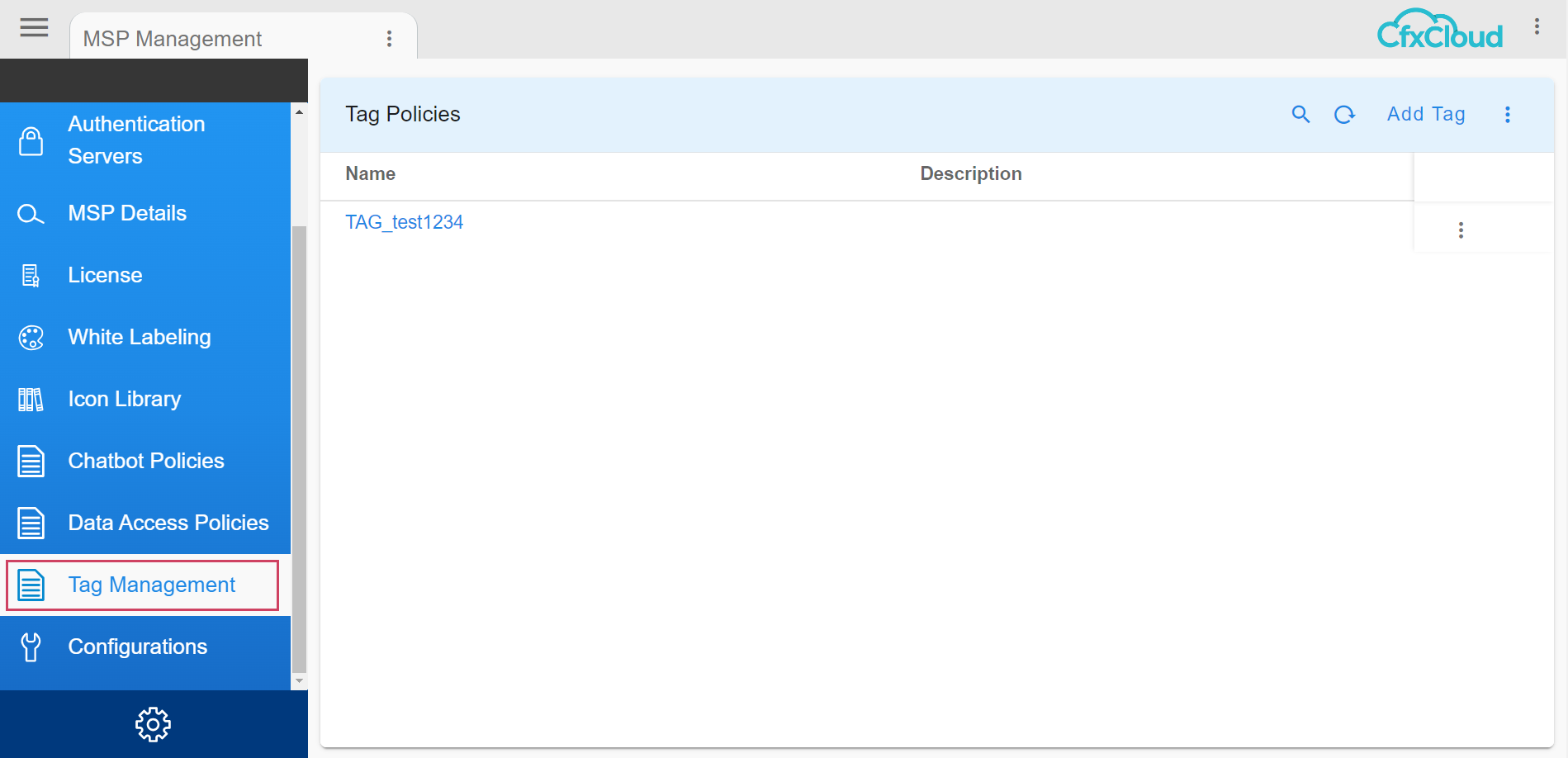
Login as user with MSP Admin role and go to Menu -> Administration -> Tag Management
After you click Tag Management user would have the option to Add Tag on the top right side as shown in the screenshot below where Name and Description can be added and saved
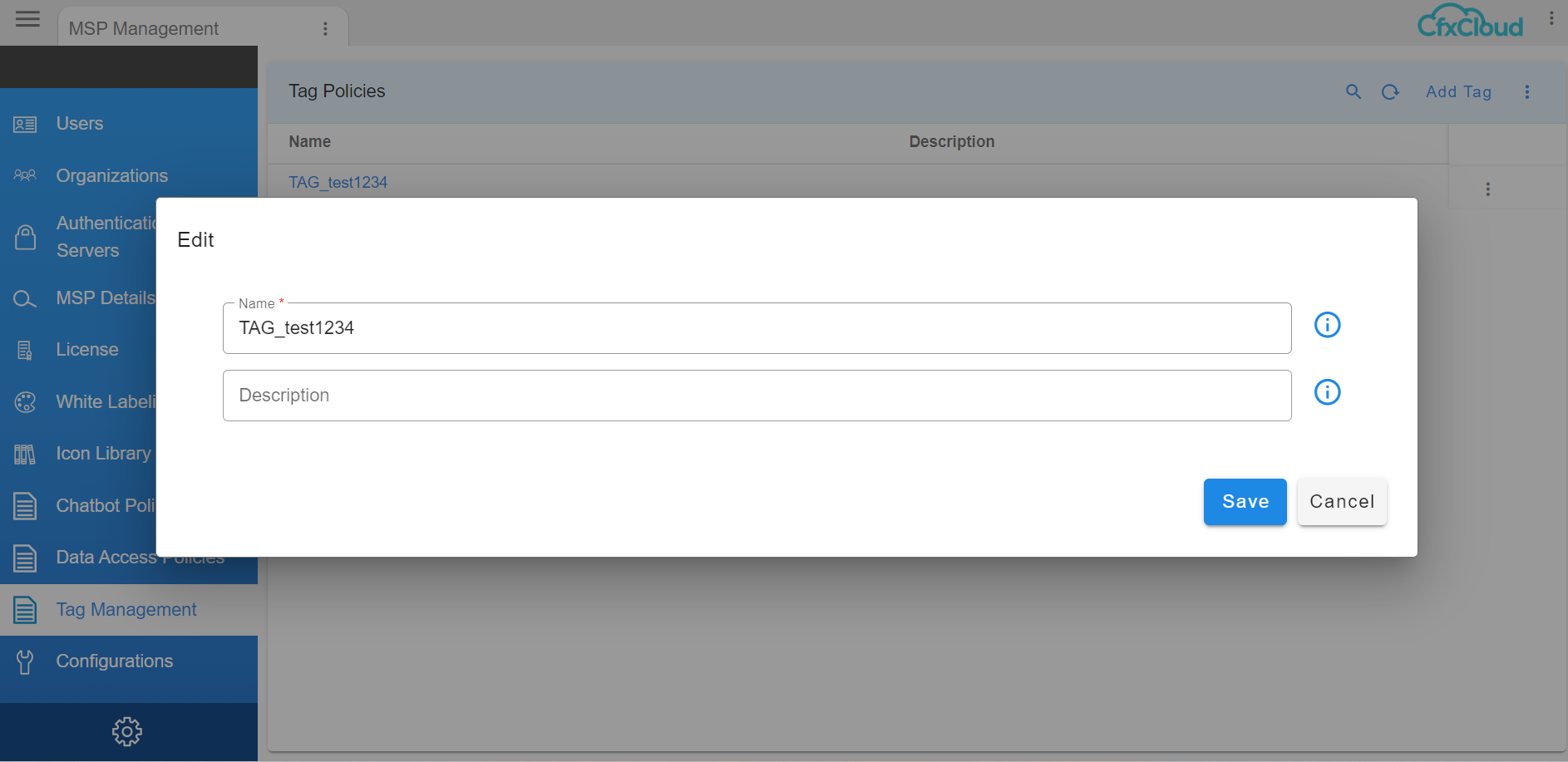
6.2 Edit Tag
If the added tag description needs to be edited, user will have the option on the top right side as shown in the screenshot below to edit the Description
After Adding Tag user would have the ability to edit description only for the added tag
6.3 Two Methods to Assign a Tag
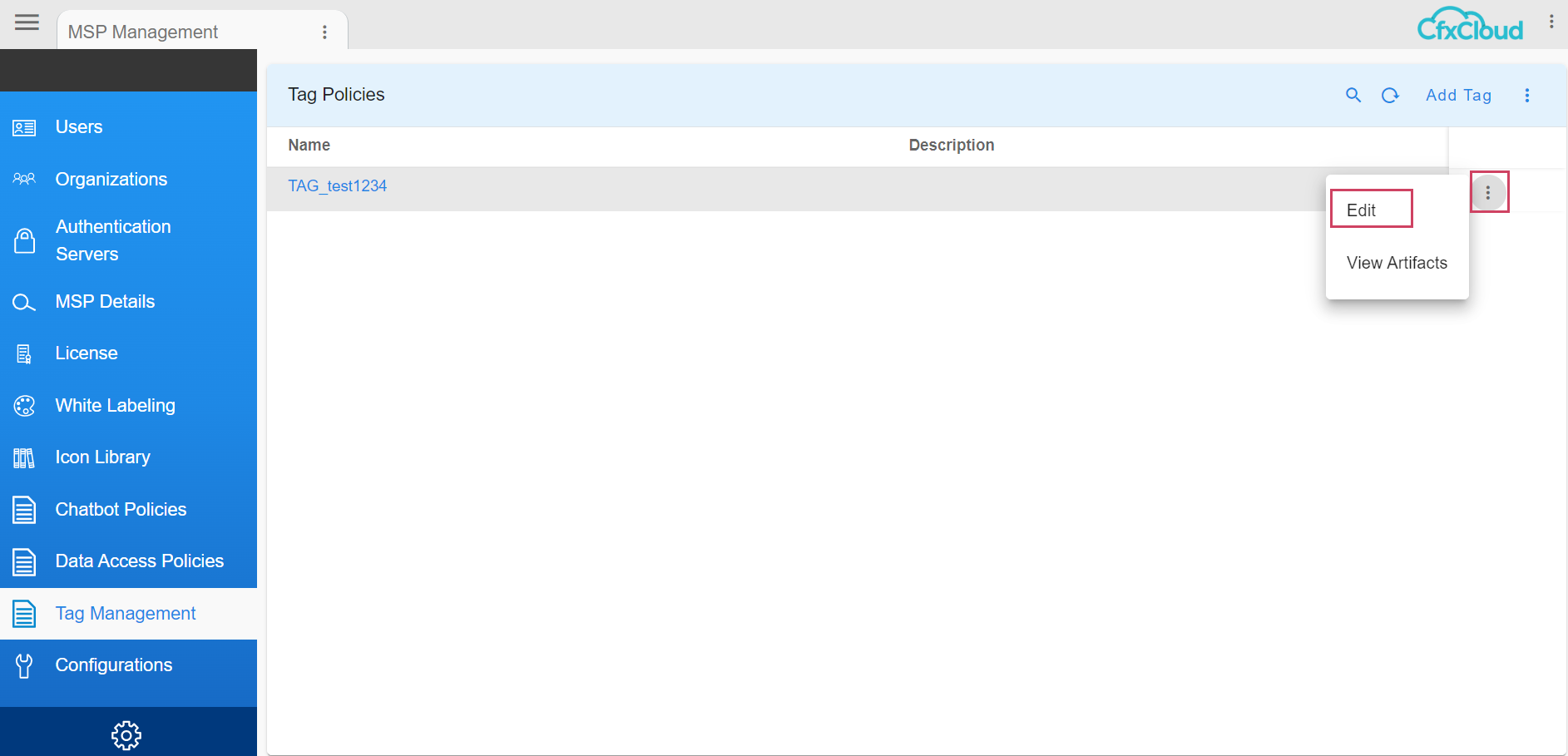
6.3.1 Method One
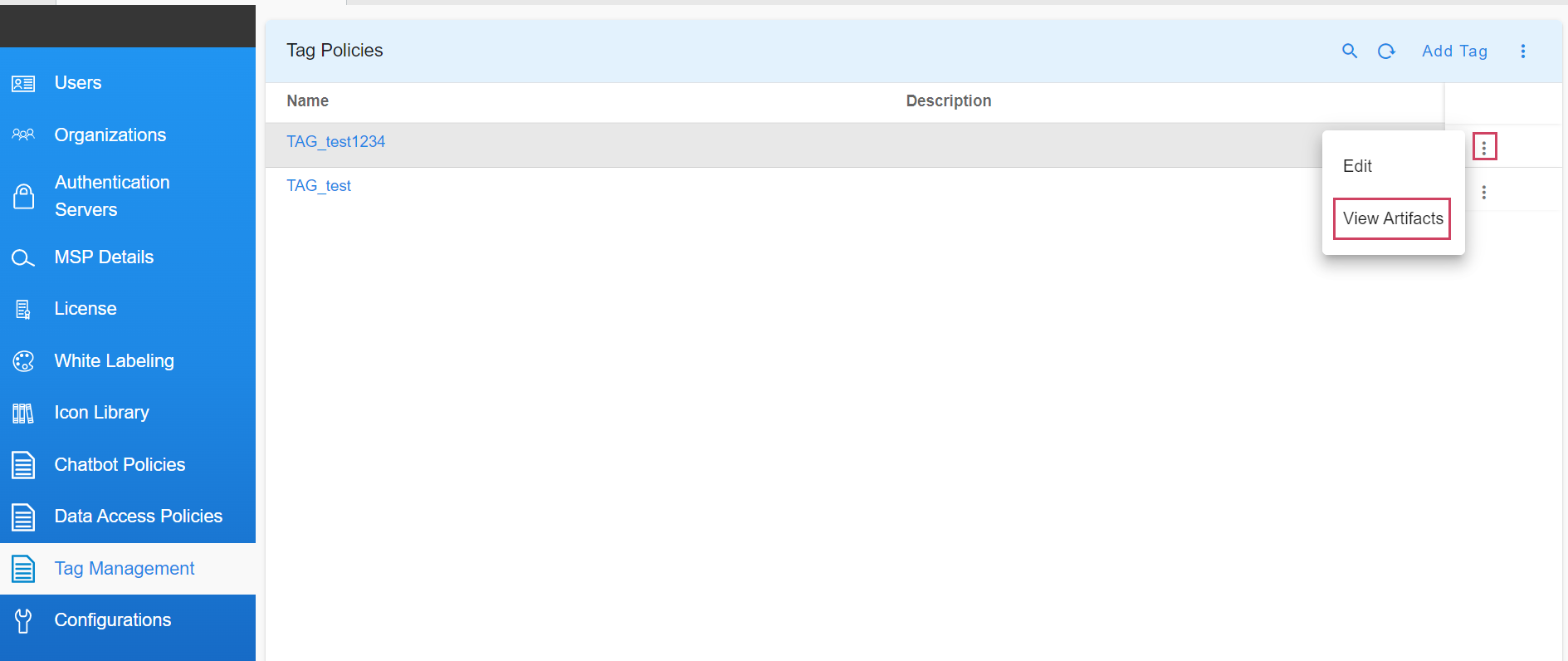
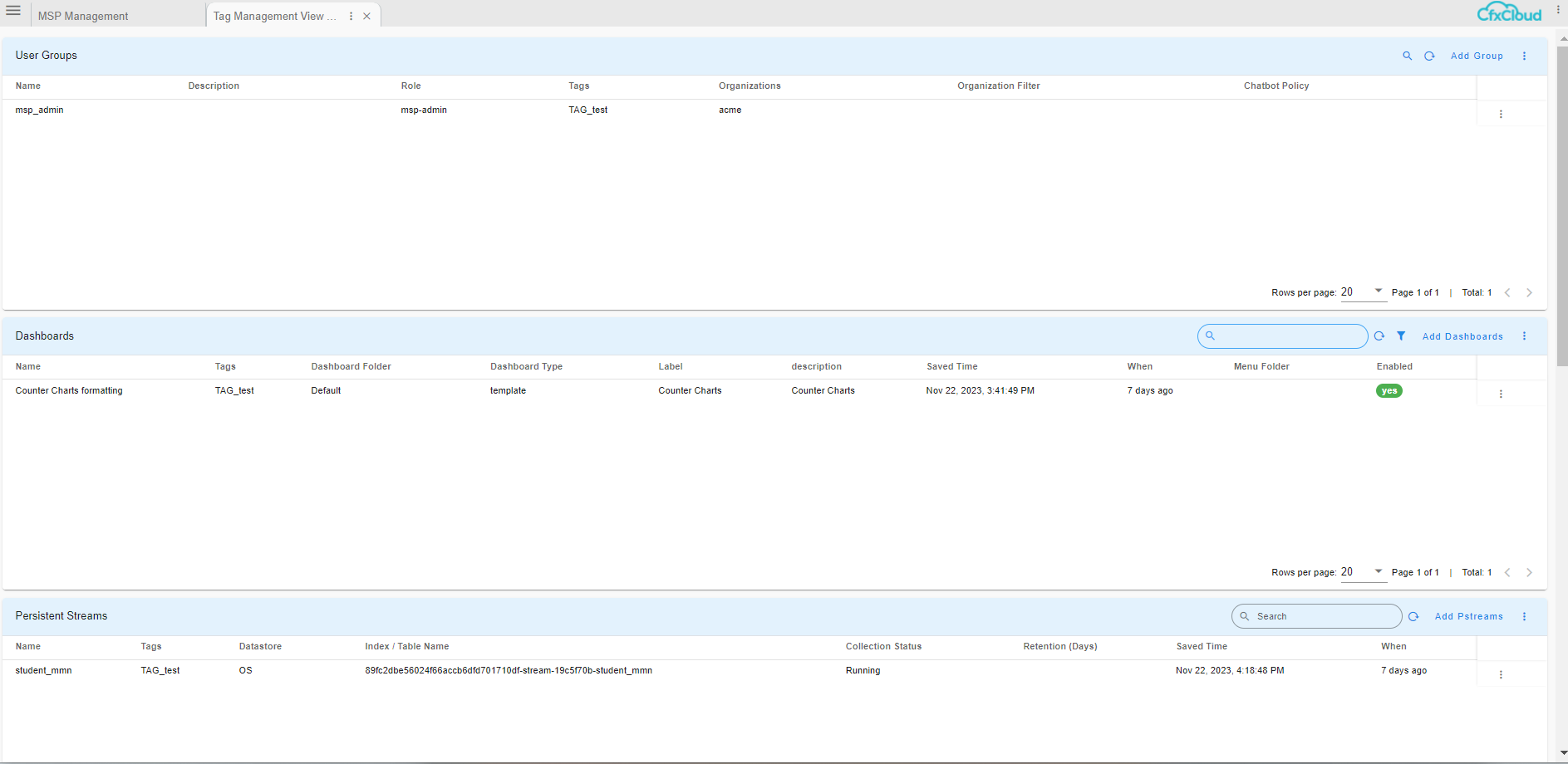
- User needs to click on the Row Action and click on View Artifacts
View Artifacts action shows the artifacts with that particular tag. The following tables are shown:
-
User Groups : List of user groups with that particular tag
-
Dashboards : List of user groups with that particular tag
-
Persistant Streams : List of pstreams with that particular tag
-
Datasets : List of datasets with that particular tag
-
Credentials : List of credentials with that particular tag
User can pick a name from that particular Artifacts list and Assign a Tag
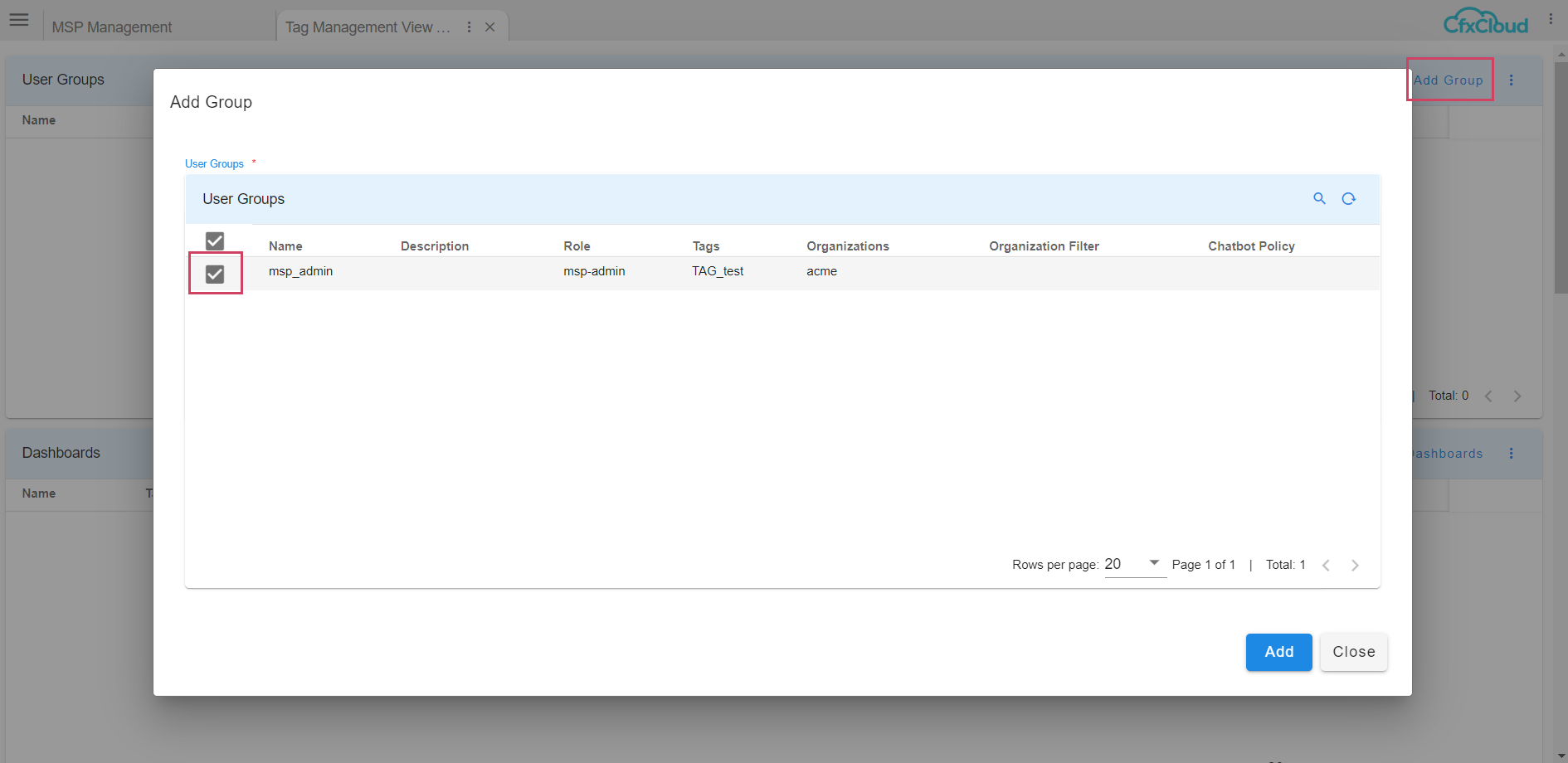
To assign tag to a user group user can click on Add Group and Click on the Group to assign the Tag as Shown below in the screenshot
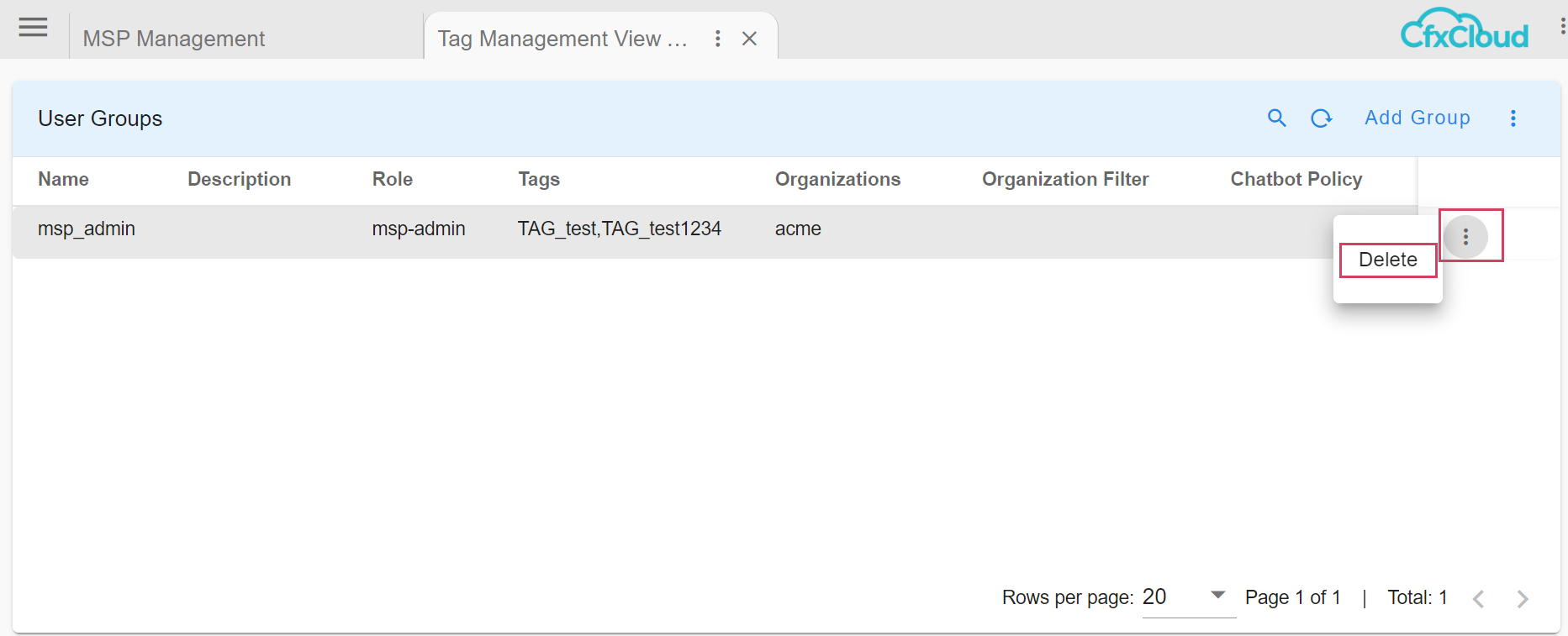
To delete Tag from user group user can click on delete
Note
We can Follow the same procedure to Add and Delete Tags for other Artifacts such as Dashboards, Persistant Streams, Datasets & Credentials
6.3.2 Method Two
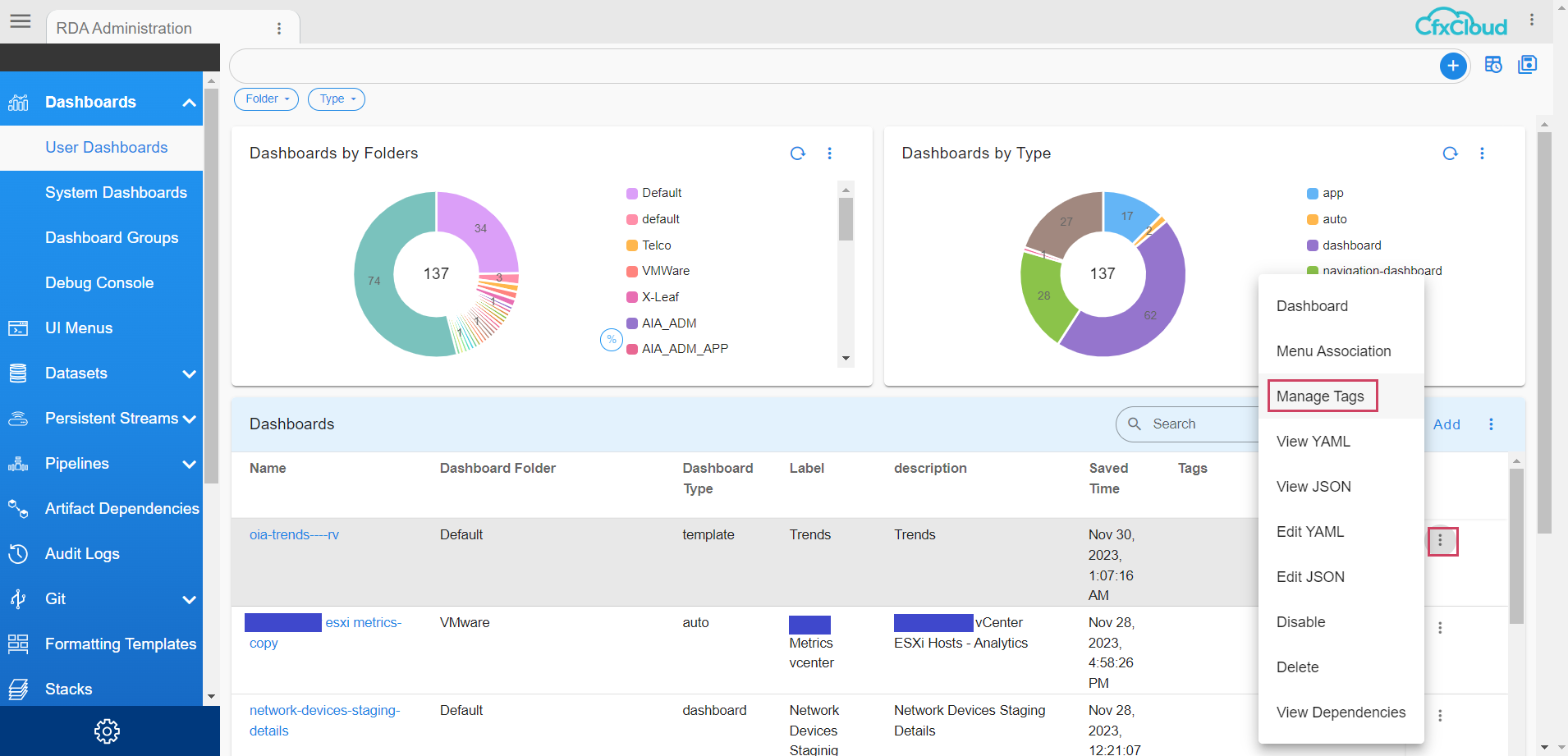
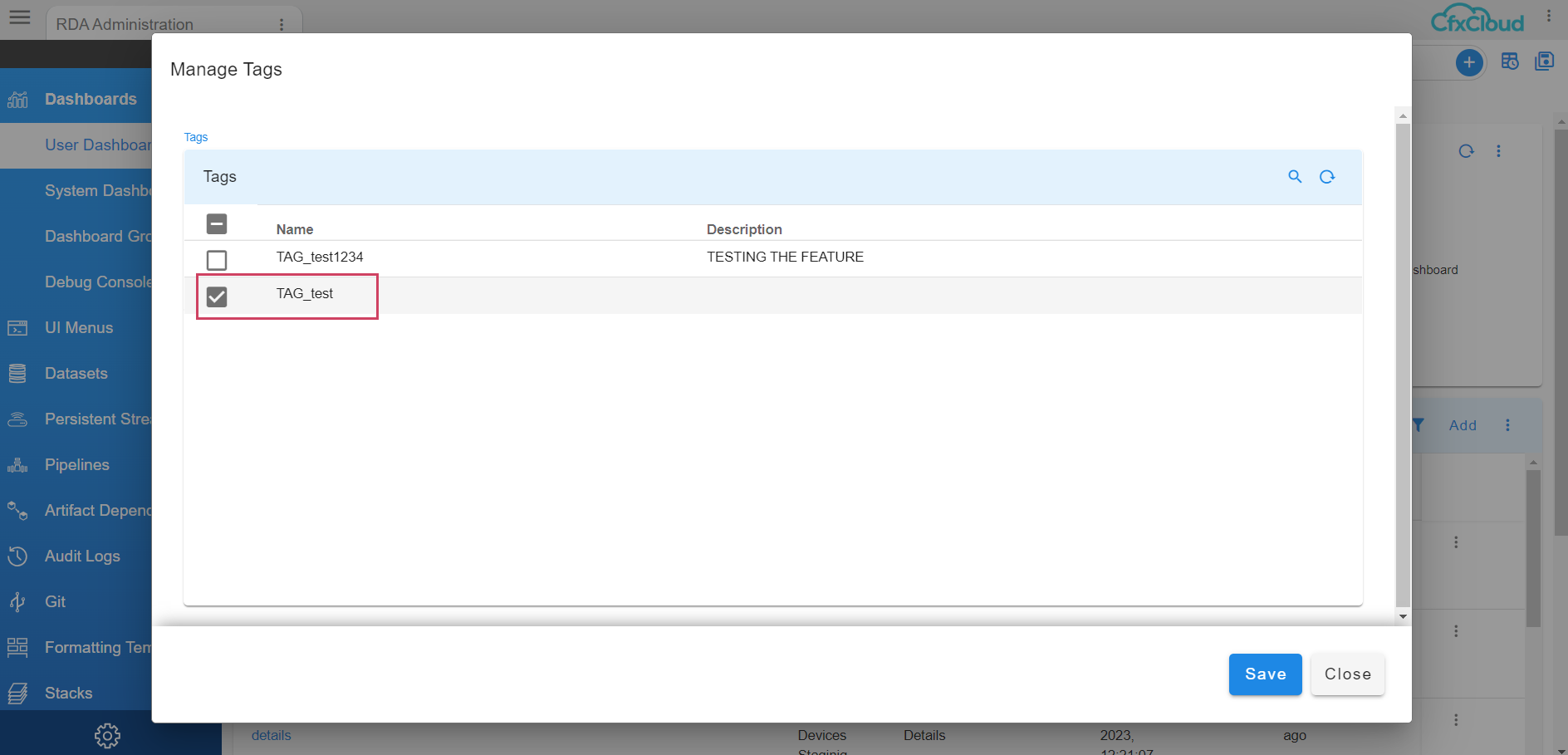
Go to Menu -> Configuration → RDA Administration click on the Row Action and select Manage Tags
Click on the Tags which the User wants to Assign
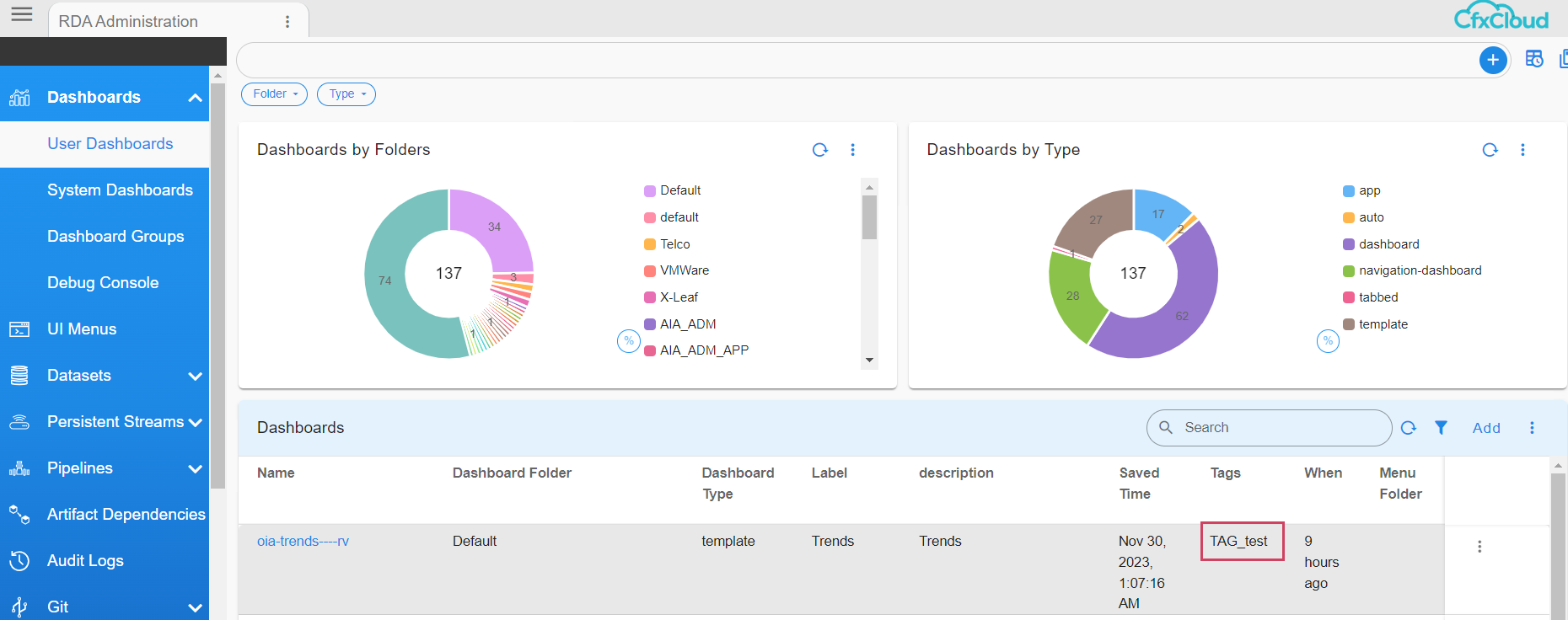
The assigned Tag can be seen as shown below in the screenshot
Note
The Method Two can be used only for Datasets , Dashboards & Credentials
7. Portal UI - System Default Landing Page
7.1 Default Homepage
When a User logs-in, the first page which shows up is the Landing Page, By default user can start the landing page in different places, User Group Level and User Level
Tip
Please click on the pictures below to enlarge and to go back to the page please click on the back arrow button on the top.
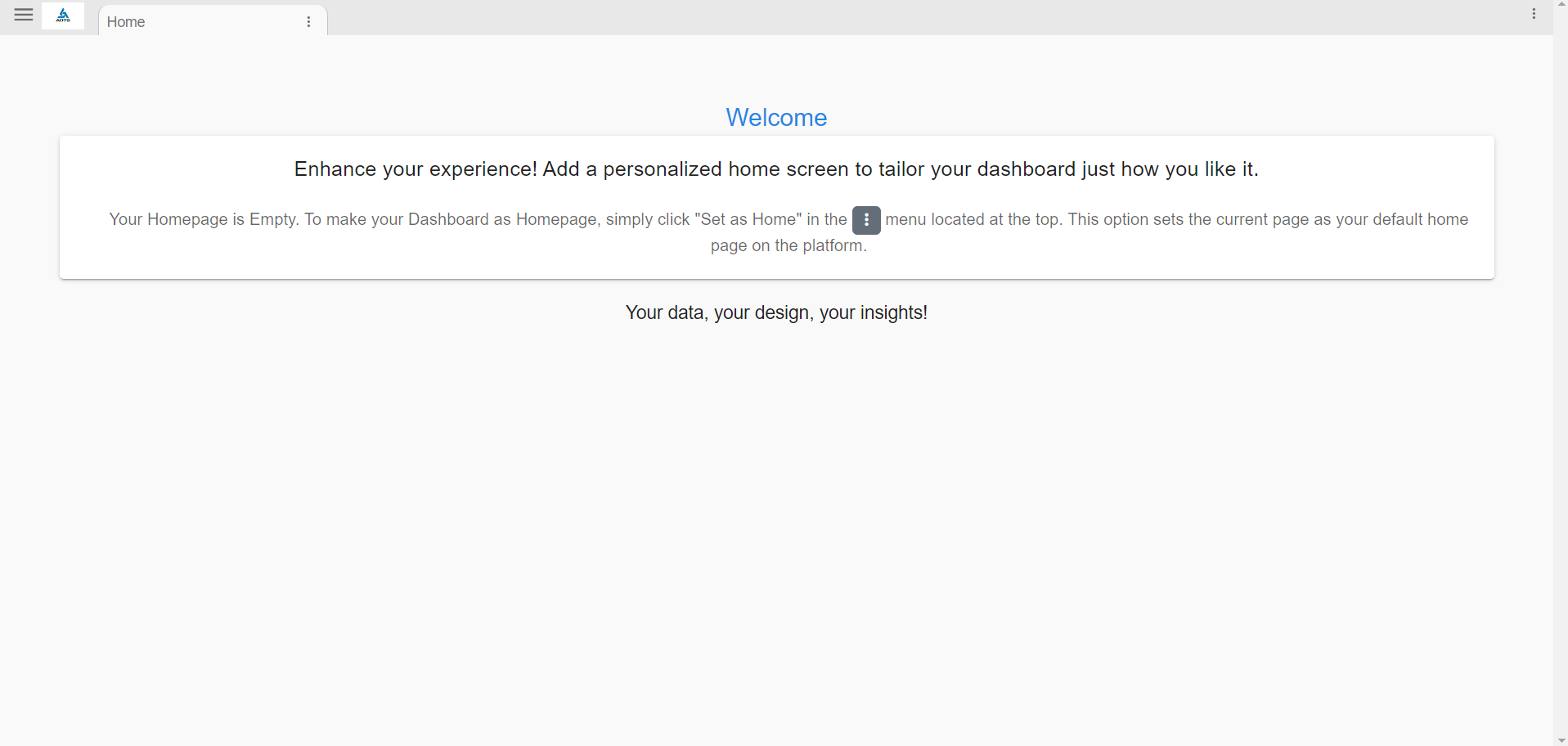
Default Landing Page would look same as shown in the screenshot shown below, when a user logs in for the first time the below home screen will be shown
7.2 User Group Level
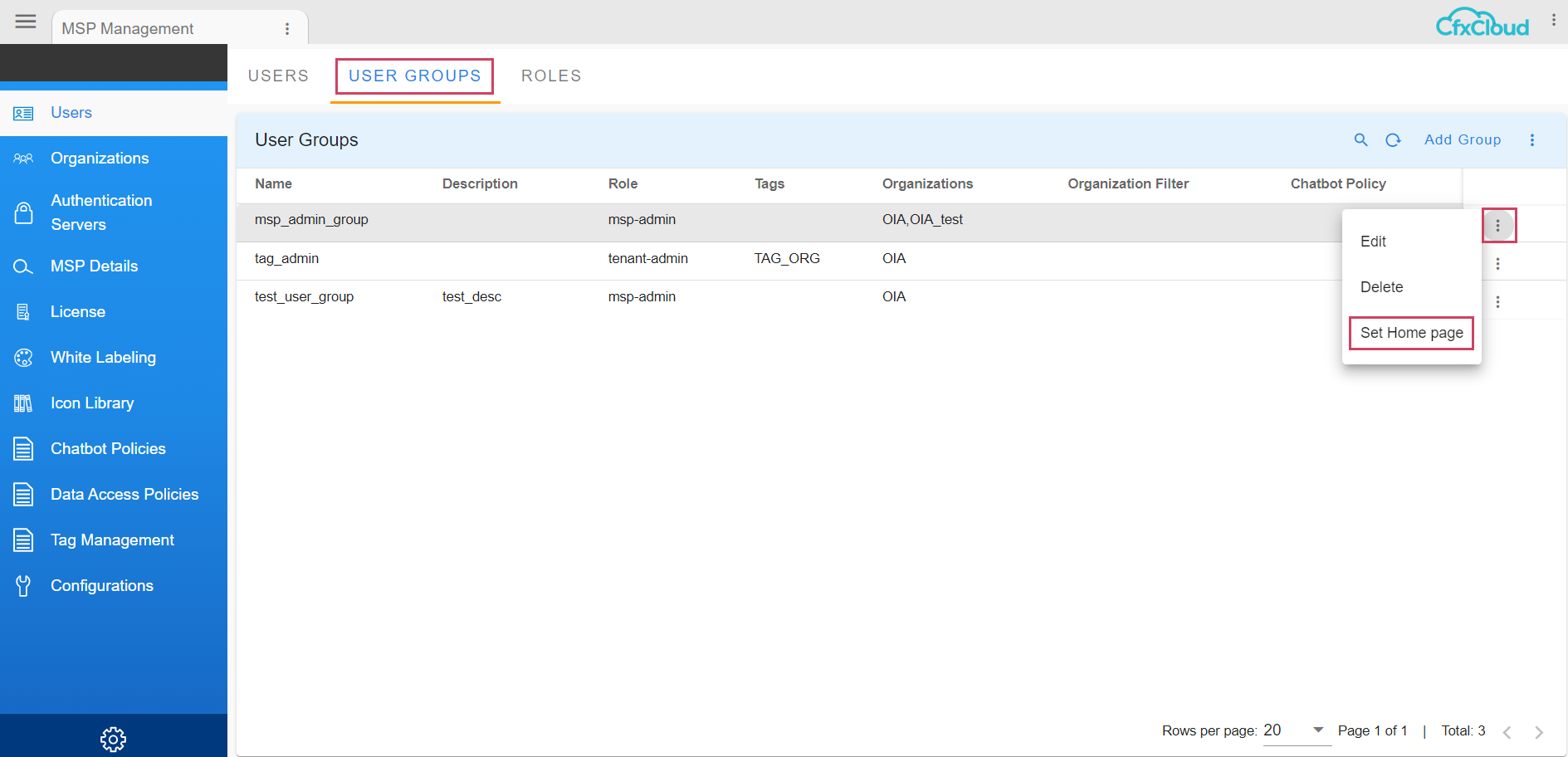
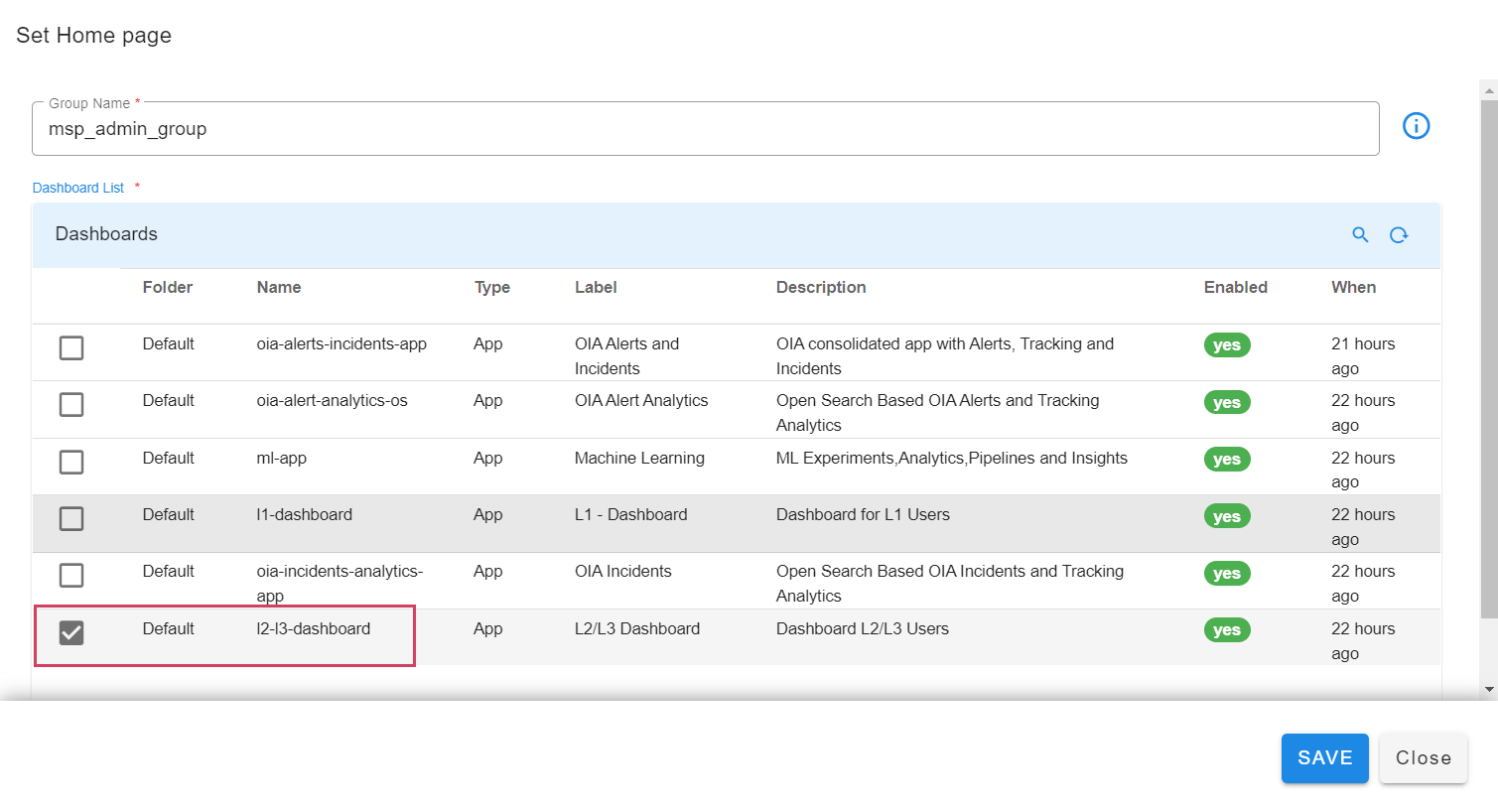
Only MSP Administrator can setup home page at User Group Level. This step sets a default home page for all users in that user group. Once logged in as MSP Administrator, Go to the top on the left click and go to Administration --> Users --> User Groups and has action then select a dashboard to be the home page and select Set Homepage all users within the user group will have the same homepage
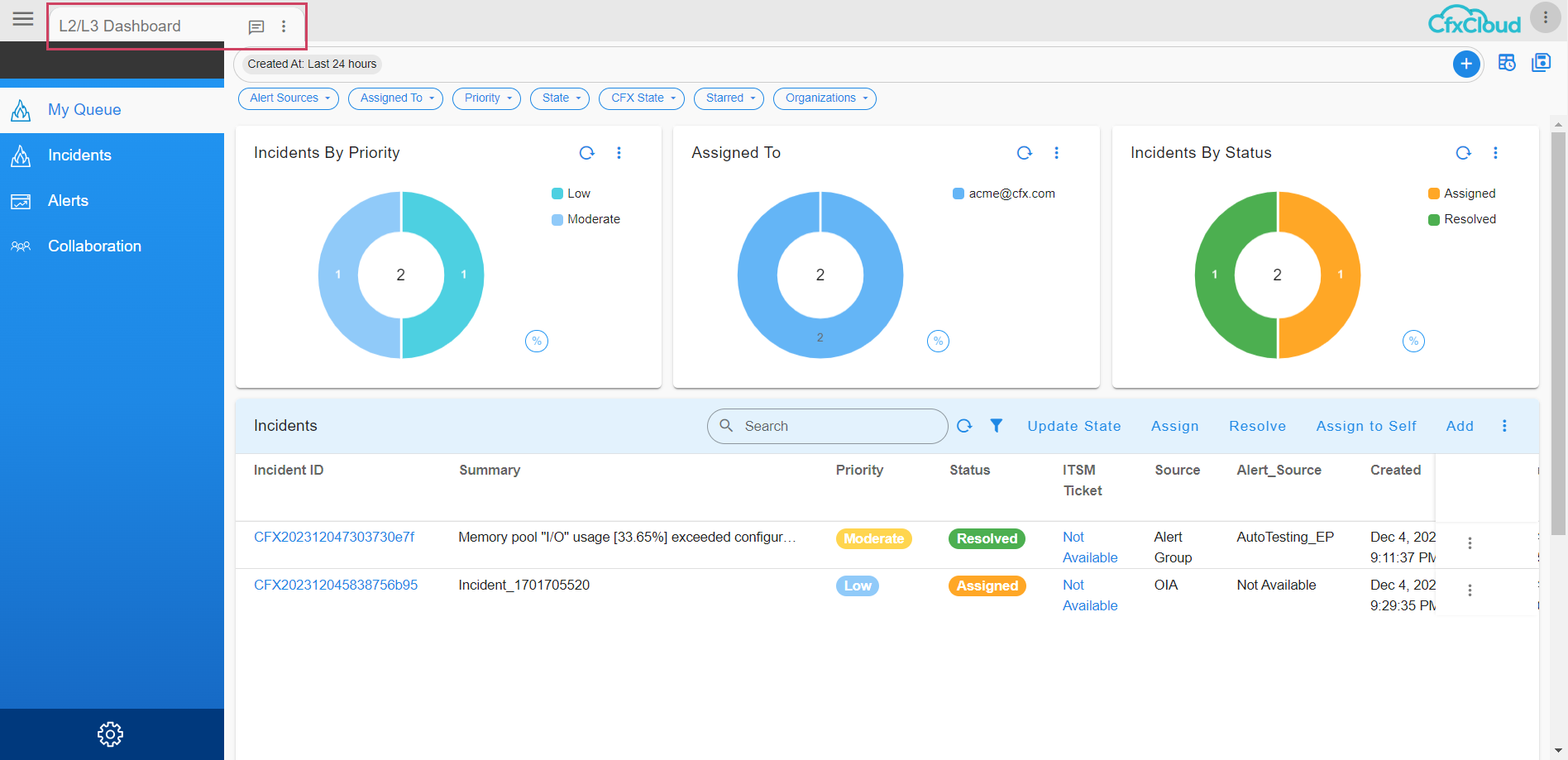
In the screenshot below user can see the selected homepage showing up when they click on Home in the left side Menu Bar.
7.3 User Level
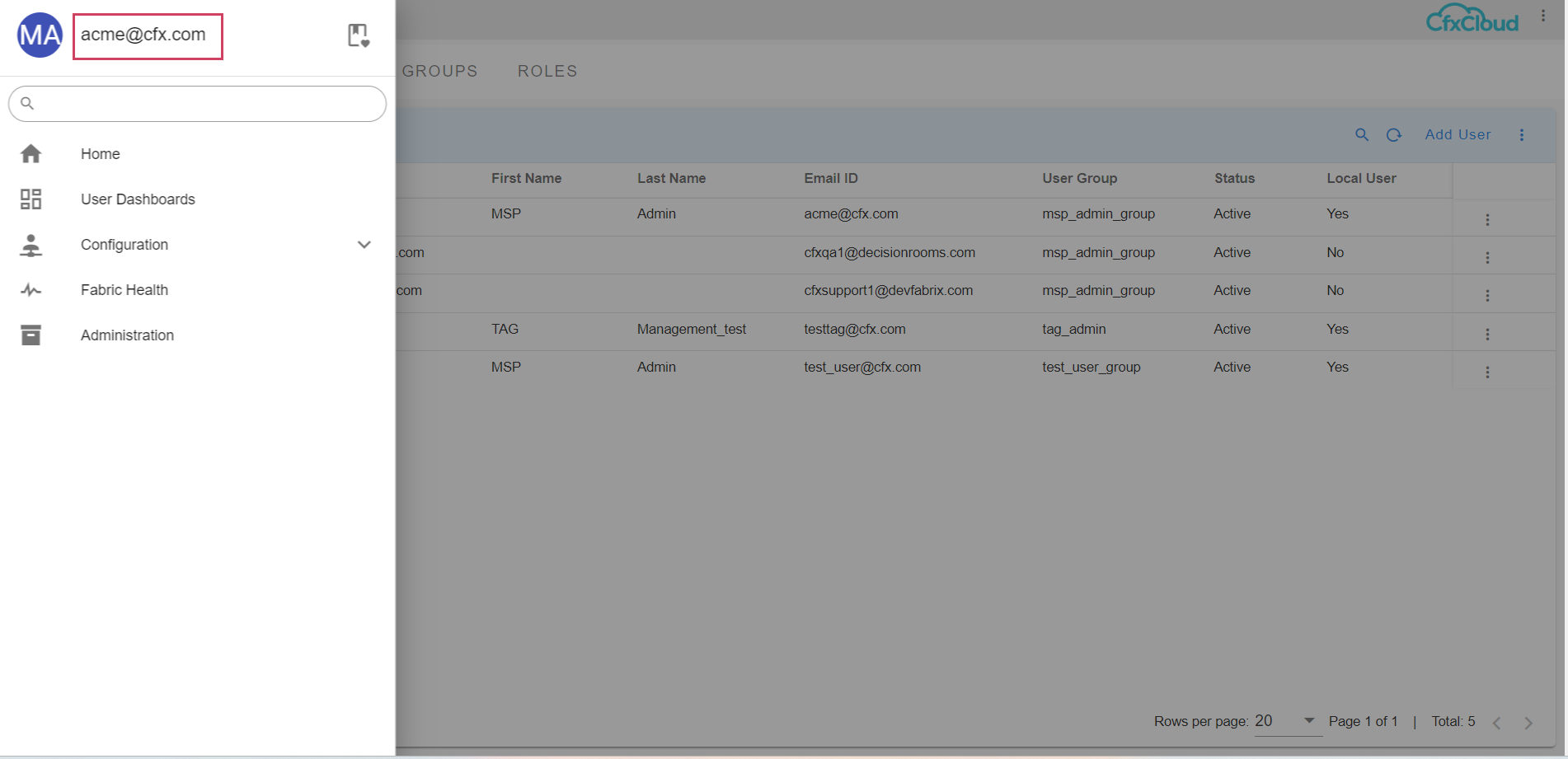
In the below screenshot a user by the name acme@cfx.com is logged in
Note
The Below step is for example purpose only, User can select any Page to set as Homepage
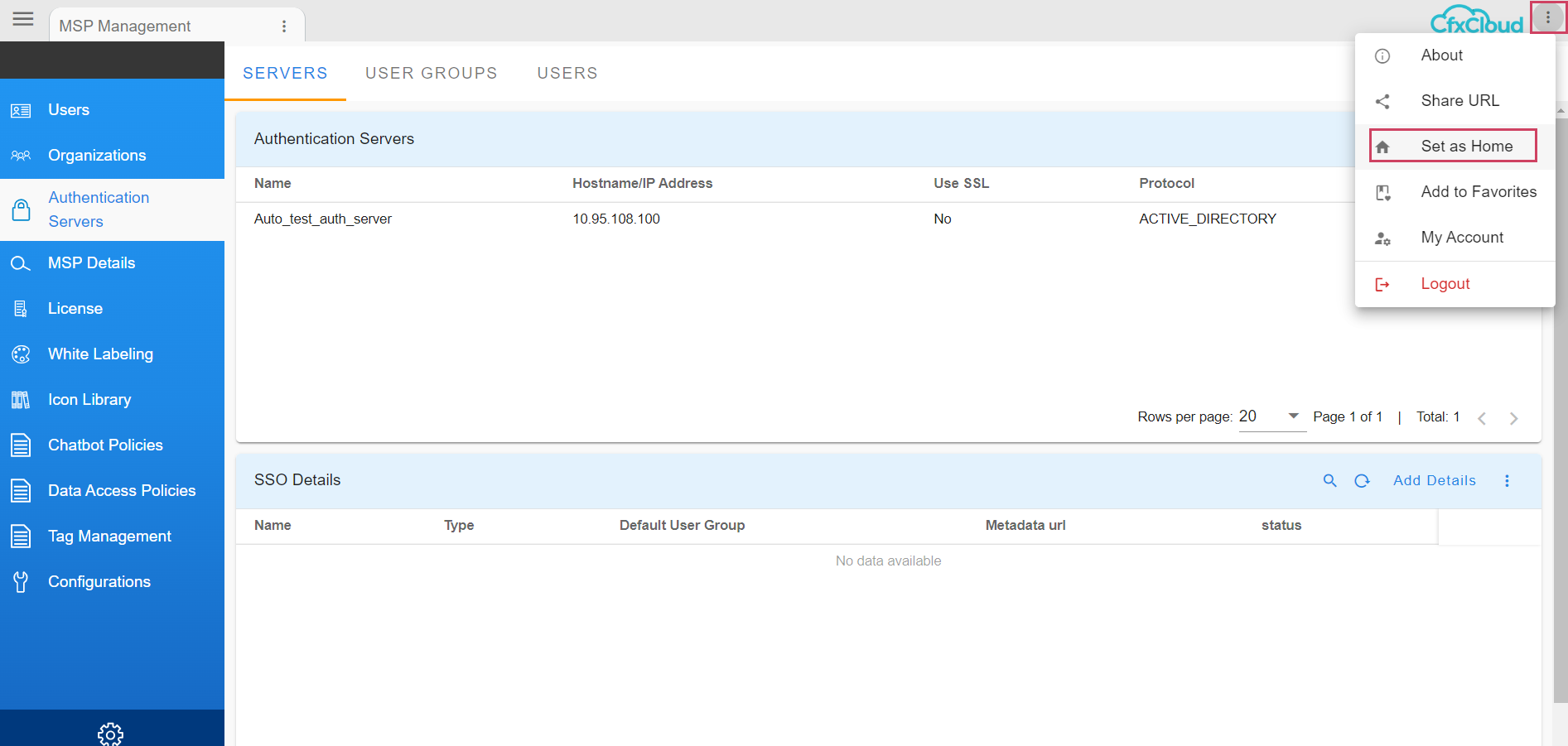
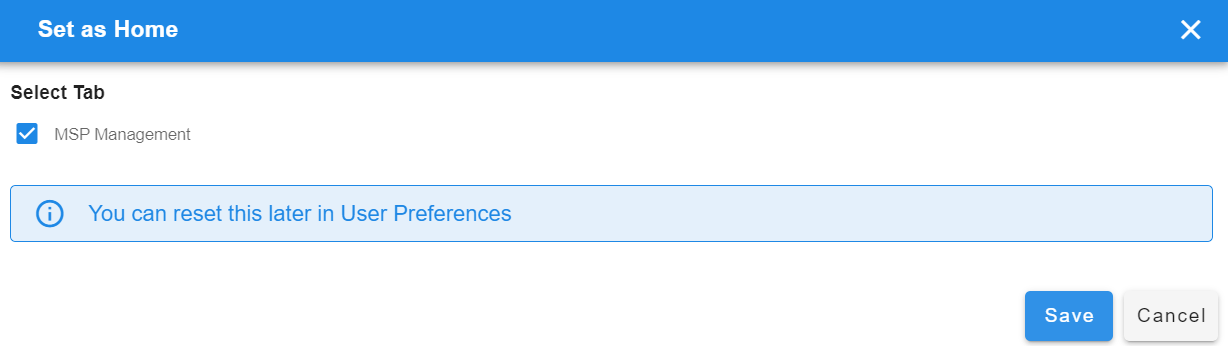
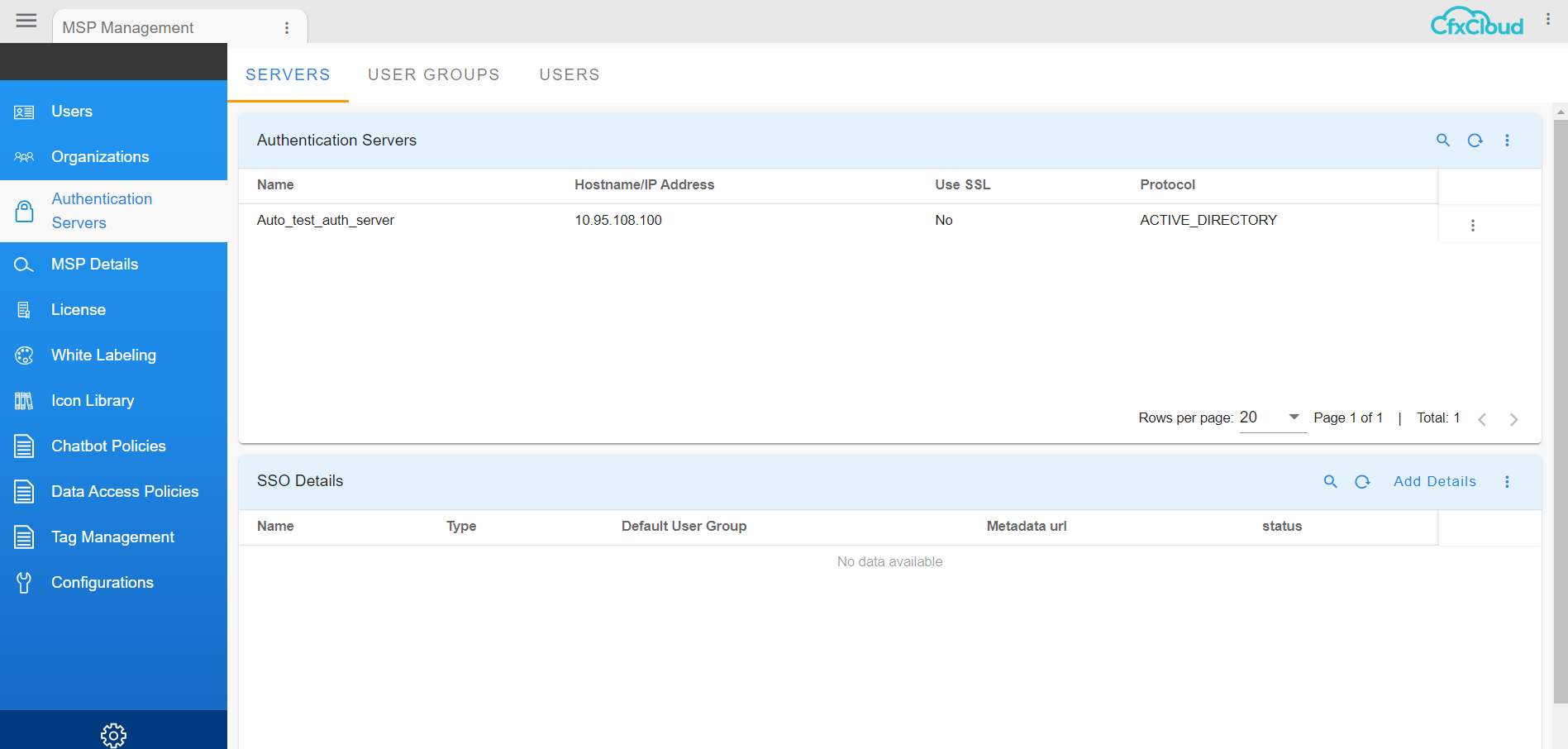
when user logs in, Menu --> Administration --> Authentication Servers --> top right side user has the option to Set as Home as shown below in the screenshot.
Here in the above screenshot the user selected Authentication Servers page as homepage and the user needs to click on Set As Home and then click on Save
Go back to the Main Menu and click on Home again, the above updated homepage can be seen here in the Below Screenshot, This way they can select any page as Homepage
7.4 Reset Default Home Page
Note
What ever the Home page user sets in the above section 9.3 will get replaced to default Homepage
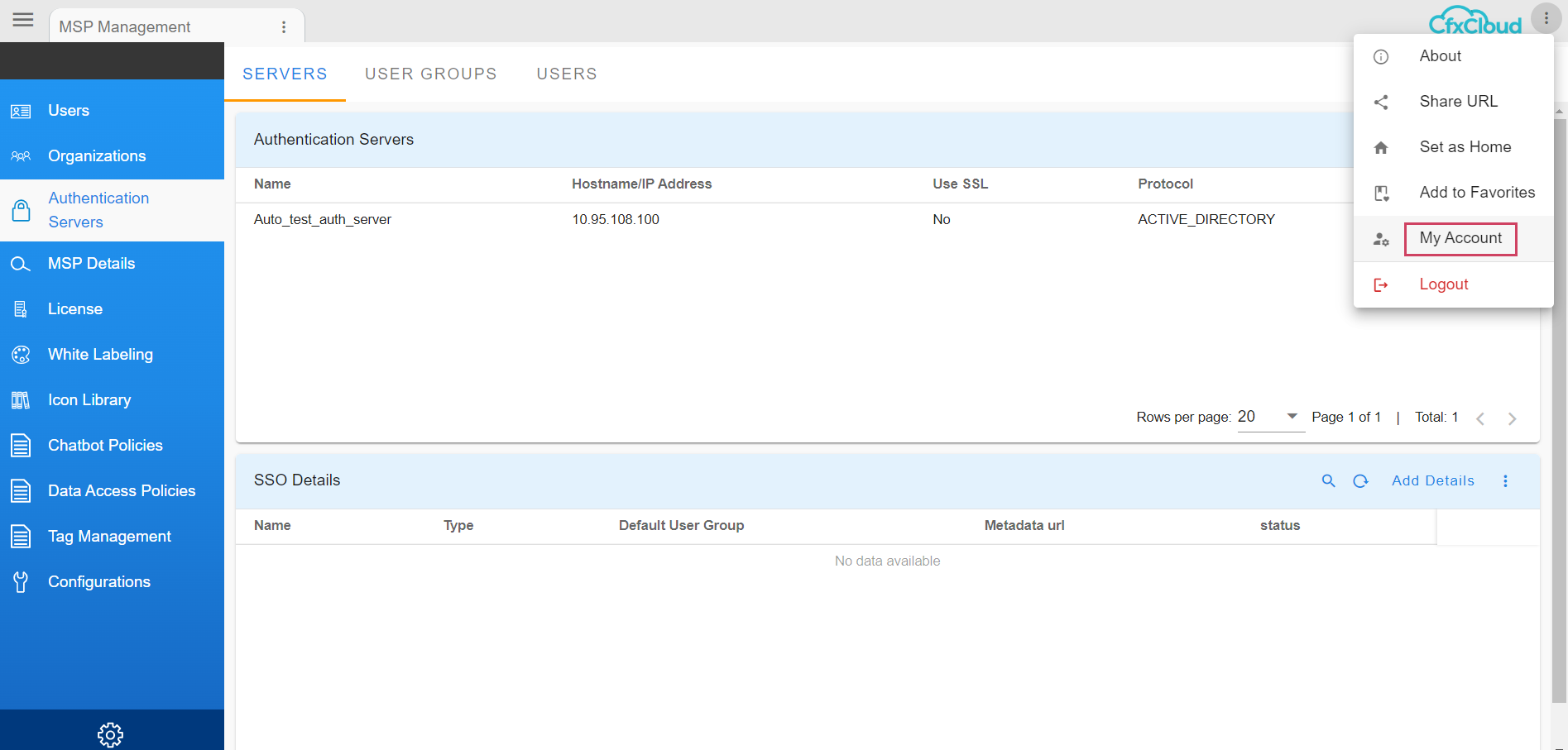
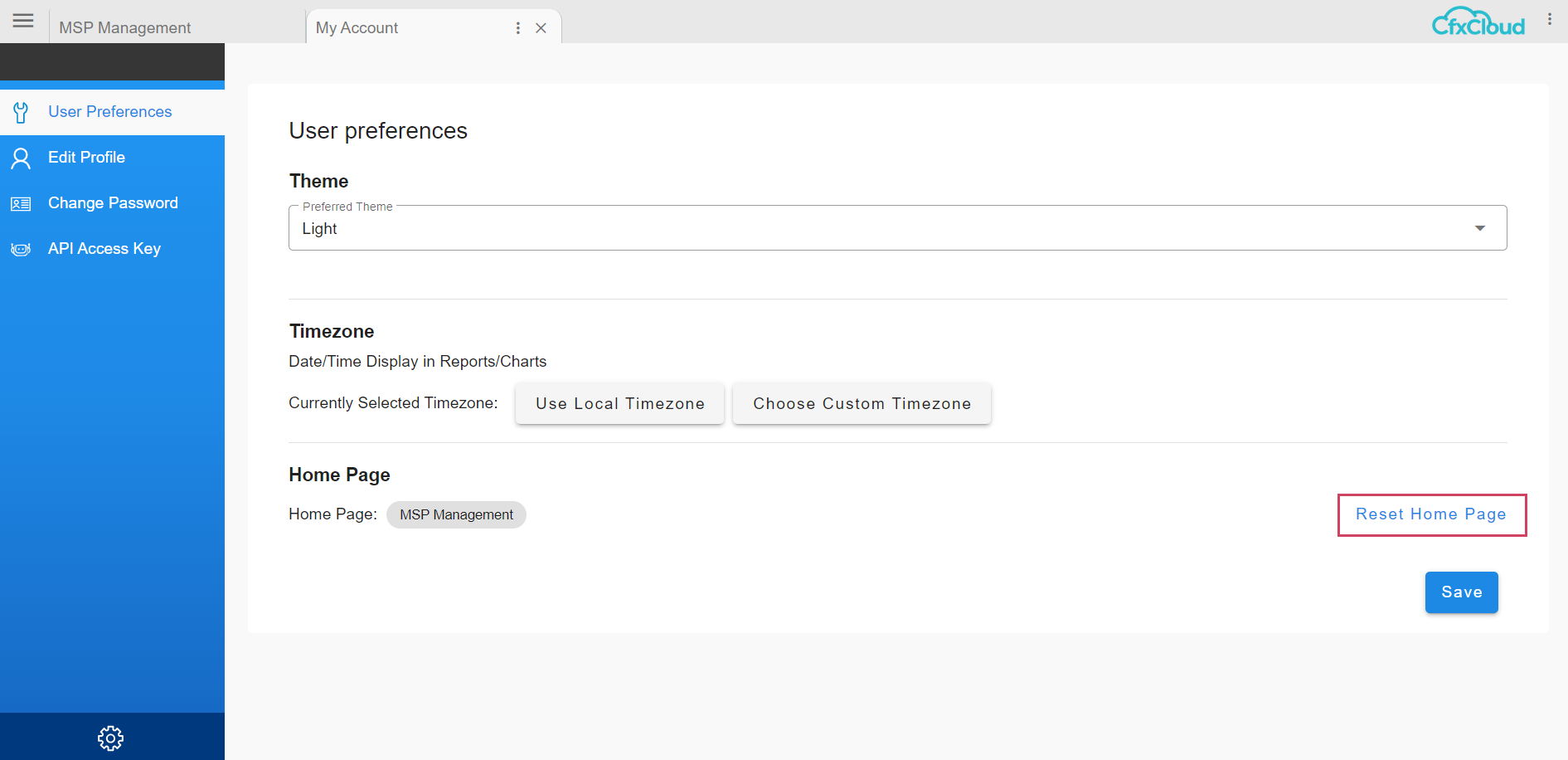
if a user wants to go back to the default home page, he needs go to top right menu as shown in the below screenshot and select My Account
The User would have the option to Reset Homepage and go back to the default Homepage, click on Reset Homepage and Save
It goes back to the Default Home page which was L2 L3 Dashboard as shown in the one of the above screenshot
8. White Labeling
8.1 White Label Settings Using Portal
To update the white-label settings using Portal go to Menu -> Administration -> White Labeling -> Login Page
8.2 White Label Settings Using RDAC Command
Overview
To update the white-label settings using the RDAC command, users must provide a whitelabelsettings.json file containing the required properties. Each field in the file supports either an image or HTML content. The system prioritizes the image field, and if the image is null, the UI will use the HTML content.
- Use the below given RDAC command
Keynotes
- Publicly Accessible Images : For the login page, users must provide publicly accessible image URLs.
- Publicly or Internally Accessible Images: For app pages or MSP logs, users can provide either publicly accessible image URLs or internal paths (e.g., /iconlib/).
{
"login_title": "Cloudfabrix Login",
"login_tab_logo_img": "",
"login_main_logo_img": "",
"login_main_logo_html": null,
"app_page_right_branding_img": "",
"app_page_right_branding_html": null,
"app_page_left_branding_img": null,
"app_page_left_branding_html": null,
"app_page_msp_logo_img": null,
"app_page_msp_logo_html": null,
"workspace_tab_logo_img": "/iconpub/cfx_dcfb5022",
"workspace_tab_title": "CloudFabrix Portal"
}
8.3 Field Descriptions
8.3.1 Login Page Properties
Properties |
Description |
Requirement |
Example |
|---|---|---|---|
| login_title | The title displayed on the browser tab | Cloudfabrix Login |
|
| login_tab_logo_img | The URL for the favicon displayed on the browser tab | Public URL or iconlib image with public access | https://example.com/favicon.ico or /iconpub/imagename |
| Login_main_logo_img | The URL for the main logo displayed on the login page | https://example.com/logo.png or /iconpub/imagename “ |
8.3.2 App Page Properties
Properties |
Description |
Requirement |
Example |
|---|---|---|---|
| app_page_right_branding_img | The URL for the right branding image on the app page | Public URL or iconlib url | "https://example.com/right_branding.png or /iconlib/image_name” |
| app_page_right_branding_html | HTML content for the right branding section if the image is not provided | " Custom Branding " |
|
| app_page_left_branding_img | The URL for the left branding image on the app page | Public URL or internal path (e.g., /iconlib/logo.png) | "/iconlib/left_branding.png" |
| app_page_left_branding_html | HTML content for the left branding section if the image is not provided. | ||
| app_page_msp_logo_img | The URL for the MSP logo displayed on the app page | Public URL or internal path | "/iconlib/msp_logo.png" |
| app_page_msp_logo_html | HTML content for the MSP logo if the image is not provided | " MSP Logo " |
|
| workspace_tab_logo_img | The URL for the favicon displayed on the app page browser tab | "/iconlib/favicon.png" | |
| workspace_tab_title | The title displayed on the app page browser tab | "Cloudfabrix Dashboard" |
8.3.3 Instructions
-
Create or update the
whitelabelsettings.jsonfile with the required properties as described above. -
Ensure that the image URLs are publicly accessible for the login page and either public or internal for the app pages.
-
Use the RDAC command to upload the
whitelabelsettings.jsonfile and apply the changes.
9. Icon Library
The Icon Library serves as a centralized, easy-to-manage collection of icons, designed for seamless reuse across your portal. Each icon is assigned a unique URL (/iconlib/name), making it simple to incorporate icons into white-labeling, dashboards, and reports.
Key features include:
-
Effortless Access: Quickly retrieve icons through their unique URLs.
-
Bulk Import & Export: Streamline your workflow by adding new icons or exporting the entire collection as needed.
-
Flexible Formats: Supports both
tar.gzandZIPfiles for importing and exporting. -
Command-Line Efficiency: Leverage RDAC commands for smooth and efficient icon management.
9.1 Importing the Icon Library
The import process allows user to upload a tar.gz file or zip file containing icons and an optional manifest.json file in archive into the system.
9.1.1 Steps to Import Single Icon
Navigation Path : Home -> Menu -> Administration -> Icon Library -> Import Icon
1. Navigate to the Administration - Icon Library page in the UI.
2. Click on Import Icon action to upload individual icon with the following formats (ex. jpeg, jpg, png, gif, ico)
3. Click the Import button to start the process.
9.1.2 Steps to Import Bulk Icons
1. Navigate to the Administration - Icon Library page in the UI.
2. Click on Import Icons action and Select the tar.gz or zip file to upload.
3. Click the Import button to start the process.
9.1.2.1 Archived file format for Bulk Import with Examples
[
{
"name": "logo",
"is_public": true,
"path": "/icons/logo_16841110.jpeg",
"id": "16841110",
"uploadedBy": "acme@cfx.com"
},
{
"name": "fabrix_logo",
"is_public": true,
"path": "/icons/fabrix_logo_f93c75bd.png",
"id": "f93c75bd",
"uploadedBy": "acme@cfx.com"
},
{
"name": "rdaf",
"is_public": true,
"path": "/icons/rdaf_3152b74d.png",
"id": "3152b74d",
"uploadedBy": "acme@cfx.com"
},
{
"name": "ingestion",
"is_public": false,
"path": "/icons/ingestion_1bcebddb.png",
"id": "1bcebddb",
"uploadedBy": "acme@cfx.com"
},
{
"name": "warning",
"is_public": false,
"path": "/icons/warning_1fc4b878.png",
"id": "1fc4b878",
"uploadedBy": "acme@cfx.com"
}
]
9.1.3 Import Behavior
-
If
manifest.jsonis present in the archive, metadata from the file will be used, and public/private access passed via arguments or form will be ignored. -
Each icon in the library is assigned a unique name, with URLs following the format
/iconlib/name. During the import process, if an icon from thetarfile has the same name as an existing icon, the system automatically generates a new name in theformat name_<UUID string>. This ensures that:- No existing icons are overwritten.
- The import continues seamlessly, without skipping icons or raising errors.
-
If manifest.json is missing, the import function expects icons to be placed in the root directory of the tar file.
-
The import function does not support multiple directories within the tar file.
9.2 Exporting the Icon Library
The export process enables you to create a tar.gz file containing the current icon library, including a manifest.json file.
9.2.1 Steps to Export
1. Navigate to the Administration -> Icon Library page in the UI and click Export Icons Action.
2. Specify the name for the exported file without extension (e.g., icon_library).
3. Click the Save button to generate the file.
4. The exported file will be added to My Downloads with the given name and can be downloaded from there.
9.3 Import and Export via RDAC Command
Please use the below mentioned command for help regarding icon library
usage:
import Import icons into the library from a zip or tar.gz file. The imported icons will be added to the Icon library
export Export the entire icon library to a specified path as a tar.gz file. The exported file will include icons and a manifest.json file with metadata
positional arguments:
subcommand icon-library sub-command
options:
-h, --help show this help message and exit
Note
To or From paths must be within the mounted directory path, e.g., /home/<any-path>
9.3.1 Import Command
Note
public parameter is optional and by default it is set to False.
Note
Refer section 9.1.2.1 for Source File Format